Microsoft on Monday revealed it took steps to disrupt phishing
operations undertaken by a “highly persistent threat actor” whose
objectives align closely with Russian state interests.
The company is tracking the espionage-oriented activity cluster
under its chemical element-themed moniker
SEABORGIUM, which it said overlaps with a hacking
group also known as Callisto[1], COLDRIVER[2], and TA446.
“SEABORGIUM intrusions have also been linked to hack-and-leak
campaigns, where stolen and leaked data is used to shape narratives
in targeted countries,” Microsoft’s threat hunting teams said[3]. “Its campaigns involve
persistent phishing and credential theft campaigns leading to
intrusions and data theft.”
Attacks launched by the adversarial collective are known to
target the same organizations using consistent methodologies
applied over long periods of time, enabling it to infiltrate the
victims’ social networks through a combination of impersonation,
rapport building, and phishing.
Microsoft said it observed “only slight deviations in their
social engineering approaches and in how they deliver the initial
malicious URL to their targets.”
Primary targets include defense and intelligence consulting
companies, non-governmental organizations (NGOs) and
intergovernmental organizations (IGOs), think tanks, and higher
education entities located in the U.S. and the U.K., and to a
lesser extent in the Baltics, the Nordics, and the Eastern
Europe.
Additional targets of interest consist of former intelligence
officials, experts in Russian affairs, and Russian citizens abroad.
More than 30 organizations and personal accounts are estimated to
have been at the receiving end of its campaigns since the start of
2022.
It all starts with a reconnaissance of potential individuals by
leveraging fake personas created on social media platforms like
LinkedIn, before establishing contact with them via benign email
missives originating from newly-registered accounts configured to
match the names of the impersonated individuals.
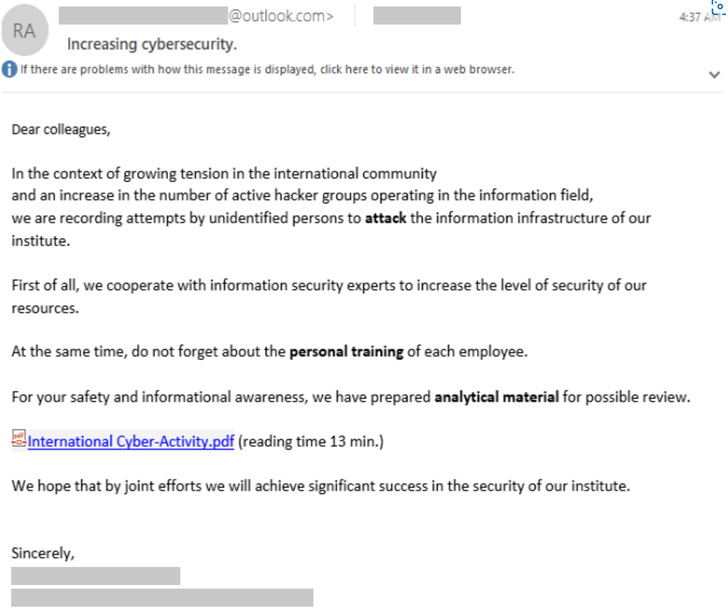
In the event the target falls victim to the social engineering
attempt, the threat actor activates the attack sequence by sending
a weaponized message embedding a booby-trapped PDF document or a
link to a file hosted on OneDrive.
“SEABORGIUM also abuses OneDrive to host PDF files that contain
a link to the malicious URL,” Microsoft said. “The actors include a
OneDrive link in the body of the email that when clicked directs
the user to a PDF file hosted within a SEABORGIUM-controlled
OneDrive account.”
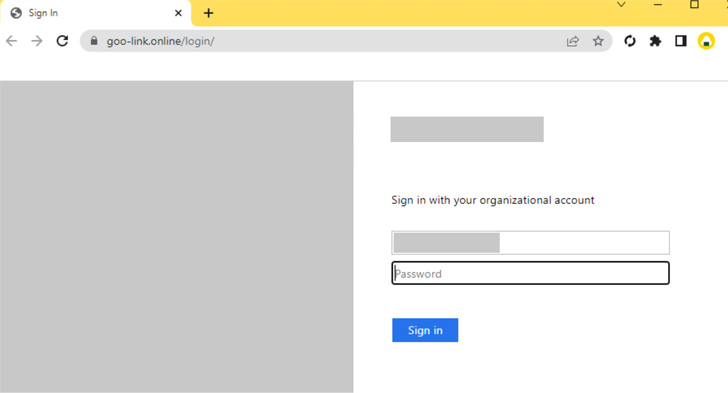
Furthermore, the adversary has been found to disguise its
operational infrastructure by resorting to seemingly harmless open
redirects to send users to the malicious server, which, in turn,
prompts users to enter their credentials to view the content.
The last phase of attacks entails abusing the stolen credentials
to access the victim’s email accounts, taking advantage of the
unauthorized logins to exfiltrate emails and attachments, set up
email forwarding rules to ensure sustained data collection and
other follow-on activities.
“There have been several cases where SEABORGIUM has been
observed using their impersonation accounts to facilitate dialog
with specific people of interest and, as a result, were included in
conversations, sometimes unwittingly, involving multiple parties,”
Redmond pointed out.
References
Read more https://thehackernews.com/2022/08/microsoft-warns-about-phishing-attacks.html