Microsoft on Thursday disclosed an “extensive series of
credential phishing campaigns” that takes advantage of a custom
phishing kit that stitched together components from at least five
different widely circulated ones with the goal of siphoning user
login information.
The tech giant’s Microsoft 365 Defender Threat Intelligence
Team, which detected the first instances of the tool in the wild in
December 2020, dubbed the copy-and-paste attack infrastructure
“TodayZoo[1].”
“The abundance of phishing kits and other tools available for
sale or rent makes it easy for a lone wolf attacker to pick and
choose the best features from these kits,” the researchers said.
“They put these functionalities together in a customized kit and
try to reap the benefits all to themselves. Such is the case of
TodayZoo.”
Phishing kits, often sold as one time payments in underground
forums, are packaged archive files containing images, scripts, and
HTML pages that enable a threat actor to set up phishing emails and
pages, using them as lures to harvest and transmit credentials to
an attacker-controlled server.
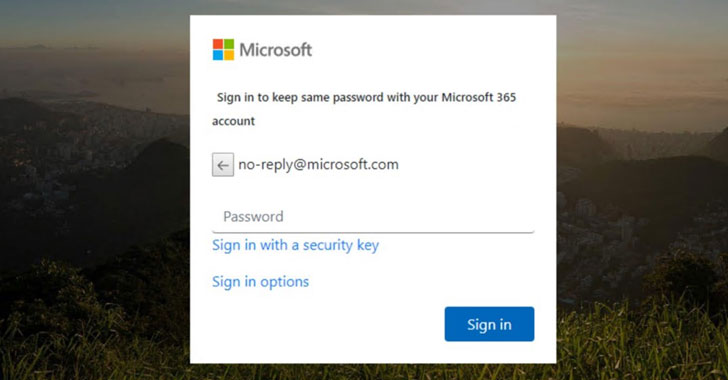
The TodayZoo phishing campaign is no different in that the
sender emails impersonate Microsoft, claiming to be password reset
or fax and scanner notifications, to redirect victims to credential
harvesting pages. Where it stands out is the phishing kit itself,
which is cobbled together out of chunks of code taken from other
kits — “some available for sale through publicly accessible scam
sellers or are reused and repackaged by other kit resellers.”
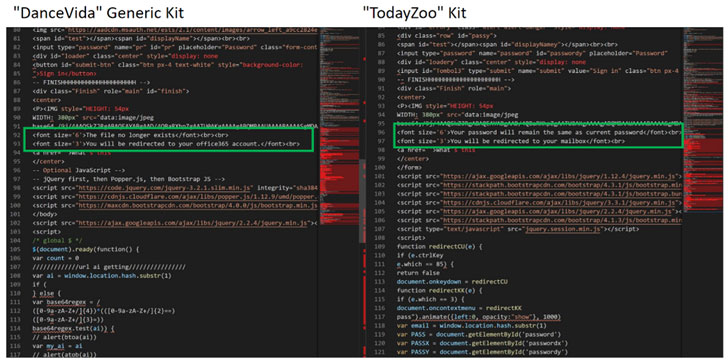
Specifically, large parts of the framework appear to have been
lifted generously from another kit, known as DanceVida, while
imitation and obfuscation-related components significantly overlap
with the code from at least five other phishing kits such as
Botssoft, FLCFood, Office-RD117, WikiRed, and Zenfo. Despite
relying on recycled modules, TodayZoo deviates from DanceVida in
the credential harvesting component by replacing the original
functionality with its own exfiltration logic.
If anything, the “‘Frankenstein’s monster characteristic of
TodayZoo” illustrates the diverse ways threat actors leverage
phishing kits for nefarious purposes, whether be it by renting them
from phishing-as-a-service (PhaaS[2]) providers or by
building their own variants from the ground up to suit their
objectives.
“This research further proves that most phishing kits observed
or available today are based on a smaller cluster of larger kit
‘families,'” Microsoft’s analysis read. “While this trend has been
observed previously, it continues to be the norm, given how
phishing kits we’ve seen share large amounts of code among
themselves.”