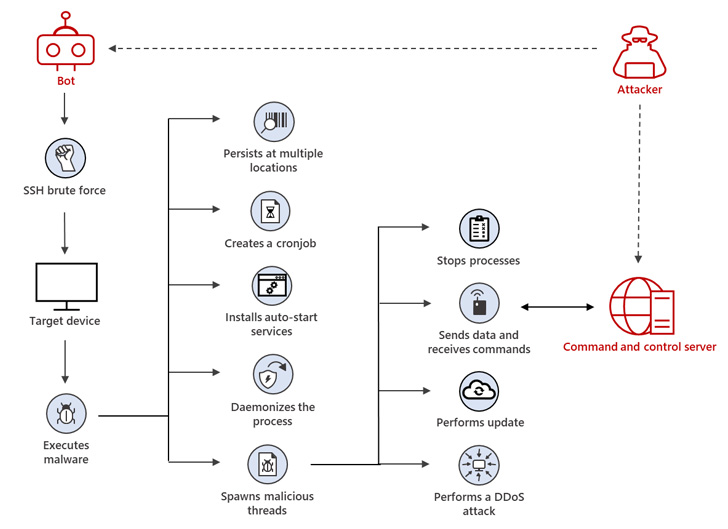
A Linux botnet malware known as XorDdos has witnessed a
254% surge in activity over the last six months, according to
latest research from Microsoft.
The trojan, so named for carrying out denial-of-service attacks
on Linux systems and its use of XOR-based encryption for
communications with its command-and-control (C2) server, is
known[1]
to have been active[2]
since at least 2014.
“XorDdos’ modular nature provides attackers with a versatile
trojan capable of infecting a variety of Linux system
architectures,” Ratnesh Pandey, Yevgeny Kulakov, and Jonathan Bar
Or of the Microsoft 365 Defender Research Team said[3]
in an exhaustive deep-dive of the malware.
“Its SSH brute force attacks are a relatively simple yet
effective technique for gaining root access over a number of
potential targets.”
Remote control over vulnerable IoT and other internet-connected
devices is gained by means of secure shell (SSH) brute-force
attacks, enabling the malware to form a botnet capable of carrying
distributed denial-of-service (DDoS) attacks.
Besides being compiled for ARM, x86, and x64 architectures, the
malware is designed to support different Linux distributions, not
to mention come with features to siphon sensitive information,
install a rootkit, and act as a vector for follow-on
activities.
In recent years, XorDdos has targeted[4]
unprotected Docker servers with exposed ports (2375), using
victimized systems to overwhelm a target network or service with
fake traffic in order to render it inaccessible.
XorDdos has since emerged as the top Linux-targeted threat in
2021, according to a report[5]
from CrowdStrike published earlier this January.
“XorDdos uses evasion and persistence mechanisms that allow its
operations to remain robust and stealthy,” the researchers
noted.
“Its evasion capabilities include obfuscating the malware’s
activities, evading rule-based detection mechanisms and hash-based
malicious file lookup, as well as using anti-forensic techniques to
break process tree-based analysis.”
References
Read more https://thehackernews.com/2022/05/microsoft-warns-rise-in-xorddos-malware.html