Hardware security keys—such as those from Google and Yubico—are
considered the most secure means to protect accounts from phishing
and takeover attacks.
But a new research published on Thursday demonstrates how an
adversary in possession of such a two-factor authentication (2FA)
device can clone it by exploiting an electromagnetic side-channel
in the chip embedded in it.
The vulnerability (tracked as CVE-2021-3011) allows the
bad actor to extract the encryption key or the ECDSA[1]
private key linked to a victim’s account from a FIDO Universal 2nd
Factor (U2F) device like Google Titan Key or YubiKey, thus
completely undermining the 2FA protections.
“The adversary can sign in to the victim’s application account
without the U2F device, and without the victim noticing,” NinjaLab
researchers Victor Lomne and Thomas Roche said[2]
in a 60-page analysis.
“In other words the adversary created a clone of the U2F device
for the victim’s application account. This clone will give access
to the application account as long as the legitimate user does not
revoke its second factor authentication credentials.”
The whole list of products impacted by the flaw includes all
versions of Google Titan Security Key (all versions), Yubico
Yubikey Neo, Feitian FIDO NFC USB-A / K9, Feitian MultiPass FIDO /
K13, Feitian ePass FIDO USB-C / K21, and Feitian FIDO NFC USB-C /
K40.
Besides the security keys, the attack can also be carried out on
NXP JavaCard chips, including NXP J3D081_M59_DF, NXP J3A081, NXP
J2E081_M64, NXP J3D145_M59, NXP J3D081_M59, NXP J3E145_M64, and NXP
J3E081_M64_DF, and their respective variants.
The key-recovery attack, while doubtless severe, needs to meet a
number of prerequisites in order to be successful.
An actor will have first to steal the target’s login and
password of an account secured by the physical key, then stealthily
gain access to Titan Security Key in question, not to mention
acquire expensive equipment costing north of $12,000, and have
enough expertise to build custom software to extract the key linked
to the account.
“It is still safer to use your Google Titan Security Key or
other impacted products as a FIDO U2F two-factor authentication
token to sign in to applications rather than not using one,” the
researchers said.
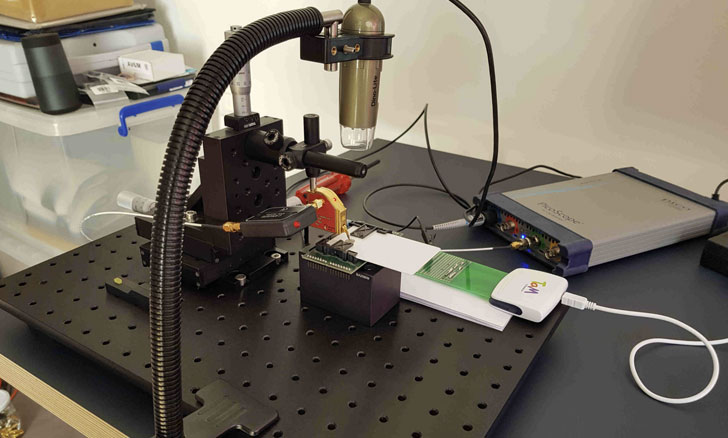
To clone the U2F key, the researchers set about the task by
tearing the device down using a hot air gun to remove the plastic
casing and expose the two microcontrollers soldered in it — a
secure enclave (NXP A700X chip) that’s used to perform the
cryptographic operations and general-purpose chip that acts as a
router between the USB/NFC interfaces and the authentication
microcontroller.
Once this is achieved, the researchers say it’s possible to
glean the ECDSA encryption key via a side-channel attack by
observing the electromagnetic radiations coming off the NXP chip
during ECDSA signatures, the core cryptographic operation of the
FIDO U2F protocol that’s performed when a U2F key is registered for the first time[3] to work with a new
account.
A side-channel attack typically works based on information
gained from the implementation of a computer system, rather than
exploiting a weakness in the software. Often, such attacks leverage
timing information, power consumption, electromagnetic leaks, and
acoustic signals as a source of data leakage.
By acquiring 6,000 such side-channel traces of the U2F
authentication request commands over a six-hour period, the
researchers said they were able to recover the ECDSA private key
linked to a FIDO U2F account created for the experiment using an
unsupervised machine learning model.
Although the security of a hardware security key isn’t
diminished by the above attack due to the limitations involved,
exploitation in the wild is not inconceivable.
“Nevertheless, this work shows that the Google Titan Security
Key (or other impacted products) would not avoid [an] unnoticed
security breach by attackers willing to put enough effort into it,”
the researchers concluded. “Users that face such a threat should
probably switch to other FIDO U2F hardware security keys, where no
vulnerability has yet been discovered.”