Telecommunications and IT service providers in the Middle East
and Asia are being targeted by a previously undocumented
Chinese-speaking threat group dubbed WIP19.
The espionage-related attacks are characterized by the use of a
stolen digital certificate issued by a Korean company called
DEEPSoft to sign malicious artifacts deployed during the
infection chain to evade detection.
“Almost all operations performed by the threat actor were
completed in a ‘hands-on keyboard’ fashion, during an interactive
session with compromised machines,” SentinelOne researchers Joey
Chen and Amitai Ben Shushan Ehrlich said[1]
in a report this week.
“This meant the attacker gave up on a stable
[command-and-control] channel in exchange for stealth.”
WIP, short for work-in-progress, is the moniker assigned by
SentinelOne to emerging or hitherto unattributed activity clusters,
similar[2]
to the UNC####, DEV-####, and TAG-## designations given by
Mandiant, Microsoft, and Recorded Future.
The cybersecurity firm also noted that select portions of the
malicious components employed by WIP19 were authored by a
Chinese-speaking malware author dubbed WinEggDrop, who has been
active since 2014.
WIP19 is said to share links to another group codenamed Operation Shadow Force[3]
owing to overlaps in the use of WinEggDrop-authored malware, stolen
certificates, and tactical overlaps.
That said, SentinelOne noted, “it is unclear whether this is a
new iteration of operation ‘Shadow Force’ or simply a different
actor utilizing similar TTPs.”
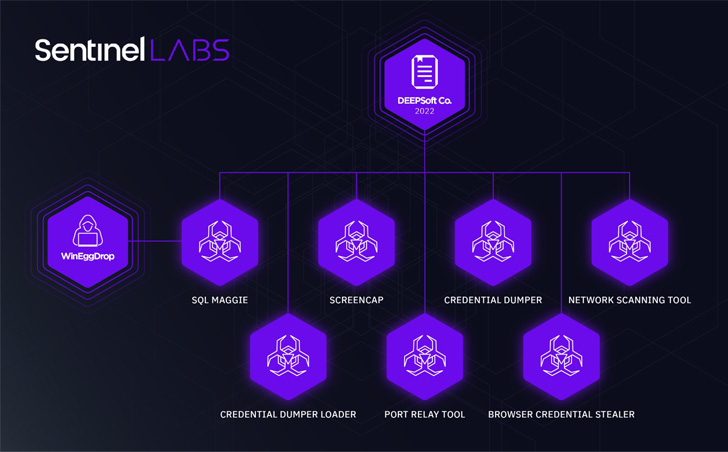
Intrusions mounted by the adversarial collective rely on a
bespoke toolset that includes a combination of a credential dumper,
network scanner, browser stealer, keystroke logger and screen
recorder (ScreenCap), and an implant known as SQLMaggie.
SQLMaggie was also the subject of an in-depth analysis by German
cybersecurity company DCSO CyTec[4]
earlier this month, calling out its ability to break into Microsoft
SQL servers and leverage the access to run arbitrary commands via
SQL queries.
An analysis of telemetry data further revealed the presence of
SQLMaggie in 285 servers spread across 42 countries, chiefly South
Korea, India, Vietnam, China, Taiwan, Russia, Thailand, Germany,
Iran, and the U.S.
The fact that the attacks are precision targeted and low in
volume, not to mention have singled out the telecom sector,
indicates that the primary motive behind the campaign may be to
gather intelligence.
The findings are yet another indication of how China-aligned
hacking groups are at once sprawling and fluid owing to the reuse
of the malware among several threat actors.
“WIP19 is an example of the greater breadth of Chinese espionage
activity experienced in critical infrastructure industries,”
SentineOne researchers said.
“The existence of reliable quartermasters and common developers
enables a landscape of hard-to-identify threat groups that are
using similar tooling, making threat clusters difficult to
distinguish from the defenders point of view.”
References
- ^
said
(www.sentinelone.com) - ^
similar
(thehackernews.com) - ^
Operation Shadow Force
(malpedia.caad.fkie.fraunhofer.de) - ^
DCSO
CyTec (medium.com)
Read more https://thehackernews.com/2022/10/new-chinese-cyberespionage-group.html