Researchers have identified functional similarities between a
malicious component used in the Raspberry Robin infection chain and
a Dridex malware loader, further strengthening the operators’
connections to the Russia-based Evil Corp group.
The findings suggest that “Evil Corp is likely using Raspberry
Robin infrastructure to carry out its attacks,” IBM Security
X-Force researcher Kevin Henson said[1]
in a Thursday analysis.
Raspberry Robin (aka QNAP Worm), first discovered[2]
by cybersecurity company Red Canary in September 2021, has remained
something of a mystery for nearly a year, partly owing to the
noticeable lack of post-exploitation activities in the wild.
That changed in July 2022 when Microsoft revealed[3]
that it observed the FakeUpdates[4]
(aka SocGholish) malware being delivered via existing Raspberry
Robin infections, with potential connections identified between
DEV-0206 and DEV-0243 (aka Evil Corp).
The malware is known to be delivered from a compromised system
via infected USB devices containing a malicious .LNK file to other
devices in the target network. The Windows Shortcut files are
designed to retrieve a malicious DLL from a remote server.
“The Raspberry Robin loaders are DLLs that decode and execute an
intermediate loader,” Henson said. “The intermediate loader
performs hook detection as an anti-analysis technique, decodes its
strings at runtime and then decodes a highly obfuscated DLL whose
purpose has not been determined.”
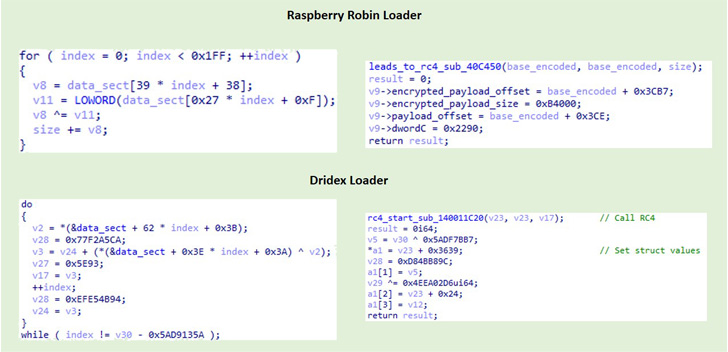
Furthermore, IBM Security X-Force’s comparative analysis of a
32-bit Raspberry Robin loader and a 64-bit Dridex loader uncovered
overlaps in functionality and structure, with both components
incorporating similar anti-analysis code and decoding the final
payload in an analogous manner.
Dridex (aka Bugat or Cridex) is the handiwork[5]
of Evil Corp and refers to a banking trojan with capabilities to
steal information, deploy additional malware such as ransomware,
and enslave compromised Windows machines into a botnet.
To mitigate Raspberry Robin infections, it’s recommended that
organizations monitor USB device connections and disable the
AutoRun feature[6]
in the Windows operating system settings.
References
- ^
said
(securityintelligence.com) - ^
discovered
(thehackernews.com) - ^
revealed
(thehackernews.com) - ^
FakeUpdates
(thehackernews.com) - ^
handiwork
(www.fortinet.com) - ^
AutoRun
feature (en.wikipedia.org)
Read more https://thehackernews.com/2022/09/new-evidence-links-raspberry-robin.html