Cybersecurity researchers have elaborated a novel attack
technique that weaponizes programmable logic controllers (PLCs[1]) to gain an initial
foothold in engineering workstations and subsequently invade the
operational technology (OT) networks.
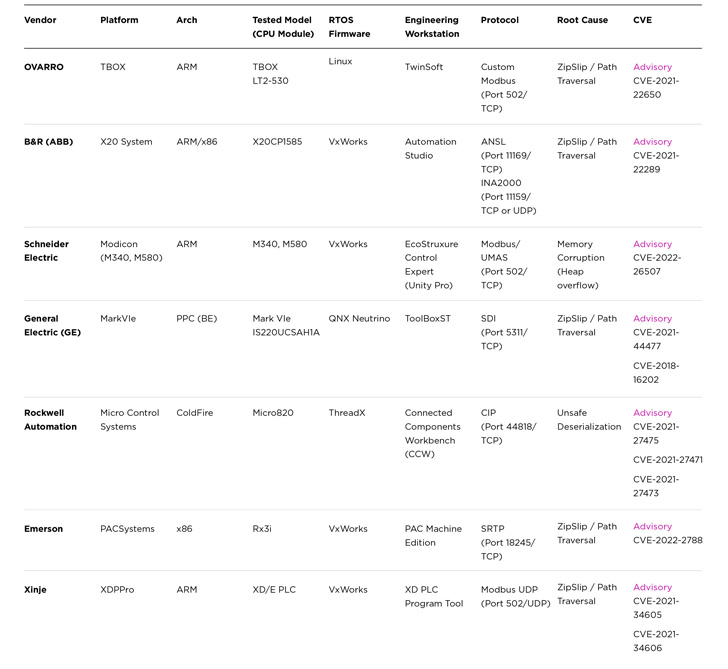
Dubbed “Evil PLC” attack by industrial security firm
Claroty, the issue impacts engineering workstation software from
Rockwell Automation, Schneider Electric, GE, B&R, Xinje,
OVARRO, and Emerson.
Programmable logic controllers (PLCs) are a crucial component of
industrial devices that control manufacturing processes in critical
infrastructure sectors. PLCs, besides orchestrating the automation
tasks, are also configured to start and stop processes and generate
alarms.
It’s hence not surprising that the entrenched access provided by
PLCs have made the machines a focus of sophisticated attacks for
more than a decade, starting from Stuxnet to PIPEDREAM[2]
(aka INCONTROLLER), with the goal of causing physical
disruptions.
“These workstation applications are often a bridge between
operational technology networks and corporate networks,” Claroty
said[3]. “An attacker who is
able to compromise and exploit vulnerabilities in an engineering
workstation could easily move onto the internal network, move
laterally between systems, and gain further access to other PLCs
and sensitive systems.”
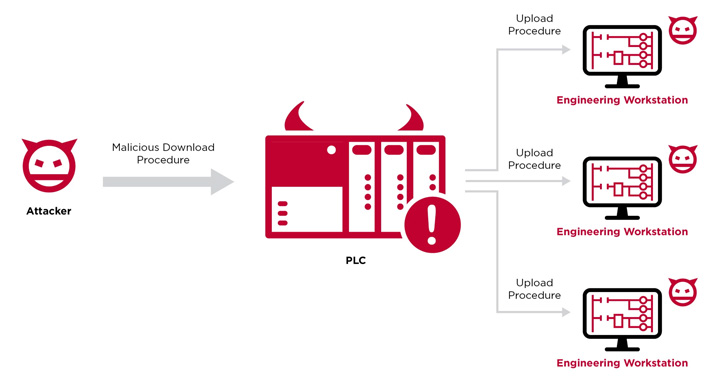
With the Evil PLC attack, the controller acts as a means to an
end, permitting the threat actor to breach a workstation, access to
all the other PLCs on the network, and even tamper with the
controller logic.
Put differently, the idea is to “use the PLC as a pivot point to
attack the engineers who program and diagnose it and gain deeper
access to the OT network,” the researchers said.
The whole sequence plays out as follows: An opportunistic
adversary deliberately induces a malfunction on an internet-exposed
PLC, an action that prompts an unsuspecting engineer to connect to
the infected PLC using the engineering workstation software as a
troubleshooting tool.
In the next phase, the bad actor leverages the previously
undiscovered flaws identified in the platforms to execute malicious
code on the workstation when an upload operation is performed by
the engineer to retrieve a working copy of the existing PLC
logic.
“The fact that the PLC stores additional types of data that are
used by the engineering software and not the PLC itself” creates a
scenario wherein the unused data stored on the PLC can be modified
to manipulate the engineering software, the researchers pointed
out.
“In most cases, the vulnerabilities exist because the software
fully trusted data coming from the PLC without performing extensive
security checks.”
In an alternative theoretical attack scenario, the Evil PLC
method can also be used as honeypots to lure threat actors into
connecting to a decoy PLC, leading to a compromise of the
attacker’s machine.
Claroty further called out the absence of security protections
in the public-facing industrial control system (ICS[4]) devices, thereby making
it easier for threat actors to alter their logic via rogue download
procedures.
To mitigate such attacks, it’s recommended to limit physical and
network access to PLCs to authorized engineers and operators,
enforce authentication mechanisms to validate the engineering
station, monitor OT network traffic for anomalous activity, and
apply patches in a timely fashion.
References
Read more https://thehackernews.com/2022/08/new-evil-plc-attack-weaponizes-plcs-to.html