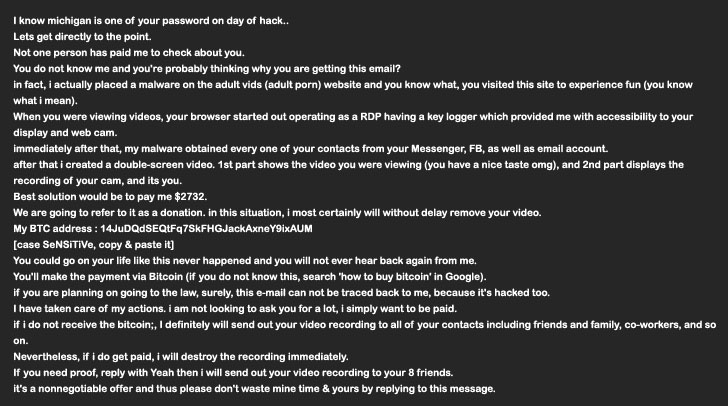
A new version of the MyloBot malware has been observed to deploy
malicious payloads that are being used to send sextortion emails
demanding victims to pay $2,732 in digital currency.
MyloBot[1], first detected in 2018,
is known to feature[2]
an array of sophisticated anti-debugging capabilities and
propagation techniques to rope infected machines into a botnet, not
to mention remove traces of other competing malware from the
systems.
Chief among its methods to evade detection and stay under the
radar included a delay of 14 days before accessing its
command-and-control servers and the facility to execute malicious
binaries directly from memory.
MyloBot also leverages a technique called process hollowing[3], wherein the attack code
is injected into a suspended and hollowed process in order to
circumvent process-based defenses. This is achieved by unmapping
the memory allocated to the live process and replacing it with the
arbitrary code to be executed, in this case a decoded resource
file.
“The second stage executable then creates a new folder under
C:\ProgramData[4],” Minerva Labs
researcher Natalie Zargarov said[5]
in a report. “It looks for svchost.exe[6]
under a system directory and executes it in suspended state. Using
an APC injection technique, it injects itself into the spawned
svchost.exe process.”
APC injection[7], similar to process
hollowing, is also a process injection technique that enables the
insertion of malicious code into an existing victim process via the
asynchronous procedure call (APC[8]) queue.
The next phase of the infection involves establishing
persistence on the compromised host, using the foothold as a
stepping stone to establish communications with a remote server to
fetch and execute a payload that, in turn, decodes and runs the
final-stage malware.
This malware is designed to abuse the endpoint to send extortion
messages alluding to the recipients’ online behaviors, such as
visiting porn sites, and threatening to leak a video that was
allegedly recorded by breaking into their computers’ webcam.
Minerva Labs’ analysis of the malware also reveals its ability
to download additional files, suggesting that the threat actor left
behind a backdoor for carrying out further attacks.
“This threat actor went through a lot of trouble to drop the
malware and keep it undetected, only to use it as an extortion mail
sender,” Zargarov said. “Botnets are dangerous exactly because of
this unknown upcoming threat. It could just as easily drop and
execute ransomware, spyware, worms, or other threats on all
infected endpoints.”
References
- ^
MyloBot
(malpedia.caad.fkie.fraunhofer.de) - ^
feature
(www.trendmicro.com) - ^
process
hollowing (attack.mitre.org) - ^
C:\ProgramData
(docs.microsoft.com) - ^
said
(blog.minerva-labs.com) - ^
svchost.exe
(en.wikipedia.org) - ^
APC
injection (attack.mitre.org) - ^
APC
(en.wikipedia.org)
Read more https://thehackernews.com/2022/02/new-mylobot-malware-variant-sends.html