Researchers have disclosed details about a security
vulnerability in the Netwrix Auditor application that, if
successfully exploited, could lead to arbitrary code execution on
affected devices.
“Since this service is typically executed with extensive
privileges in an Active Directory environment, the attacker would
likely be able to compromise the Active Directory domain,” Bishop
Fox said[1]
in an advisory published this week.
Auditor[2]
is an auditing and visibility platform that enables organizations
to have a consolidated view of their IT environments, including
Active Directory, Exchange, file servers, SharePoint, VMware, and
other systems—all from a single console.
Netwrix, the company behind the software, claims more than
11,500 customers across over 100 countries, such as Airbus, Virgin,
King’s College Hospital, and Credissimo, among others.
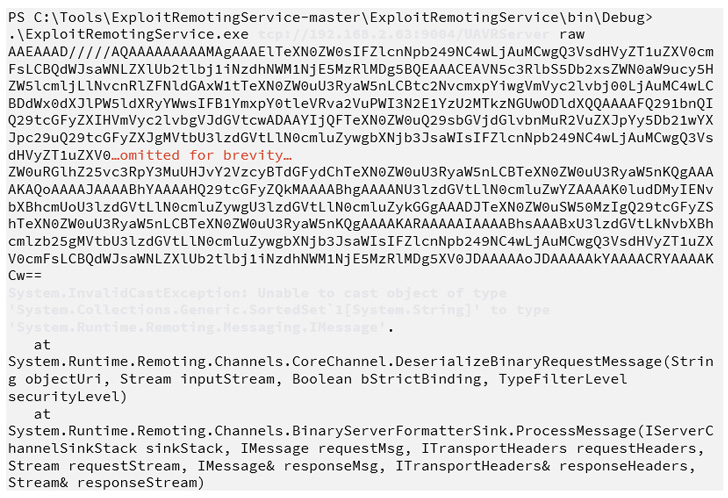
The flaw, which impacts all supported versions prior to 10.5,
has been described as an insecure object deserialization[3], which occurs when
untrusted user-controllable data is parsed to inflict remote code
execution attacks.
The root cause of the bug is an unsecured .NET remoting service
that’s accessible on TCP port 9004 on the Netwrix server, enabling
an actor to execute arbitrary commands on the server.
“Since the command was executed with NT AUTHORITY\SYSTEM
privileges, exploiting this issue would allow an attacker to fully
compromise the Netwrix server,” Bishop Fox’s Jordan Parkin
said.
Organizations relying on Auditor are recommended to update the
software to the latest version, 10.5, released on June 6, to thwart
any potential risks.
References
Read more https://thehackernews.com/2022/07/new-netwrix-auditor-bug-could-let.html