Security researchers have discovered a new vulnerability called
ParseThru affecting Golang-based applications that
could be abused to gain unauthorized access to cloud-based
applications.
“The newly discovered vulnerability allows a threat actor to
bypass validations under certain conditions, as a result of the use
of unsafe URL parsing methods built in the language,” Israeli
cybersecurity firm Oxeye said in a report[1]
shared with The Hacker News.
The issue, at its core, has to do with inconsistencies stemming
from changes introduced to Golang’s URL parsing logic that’s
implemented in the “net/url” library.
While versions of the programming language prior to 1.17 treated
semicolons as a valid query delimiter (e.g.,
example.com?a=1;b=2&c=3), this behavior has since been modified
to throw an error upon finding a query string containing a
semicolon.
“The net/url and net/http packages used to accept “;”
(semicolon) as a setting separator in URL queries, in addition to
“&” (ampersand),” according to the release
notes[2] for version 1.17
released last August.
“Now, settings with non-percent-encoded semicolons are rejected
and net/http servers will log a warning to ‘Server.ErrorLog’ when
encountering one in a request URL.”
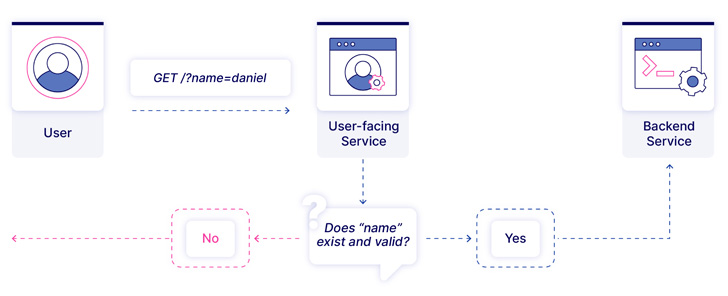
The problem arises when a Golang-based public API built upon
version 1.17 or later communicates with a backend service running
an earlier version, leading to a scenario where a malicious actor
could smuggle requests incorporating query parameters that would
otherwise be rejected.
Put simply, the idea is to send requests containing a semicolon
in the query string, which is ignored by the user-facing Golang API
but is processed by the internal service. This, in turn, is made
possible owing to the fact that one of the
methods[3] responsible for getting
the parsed query string silently discards the returned error.
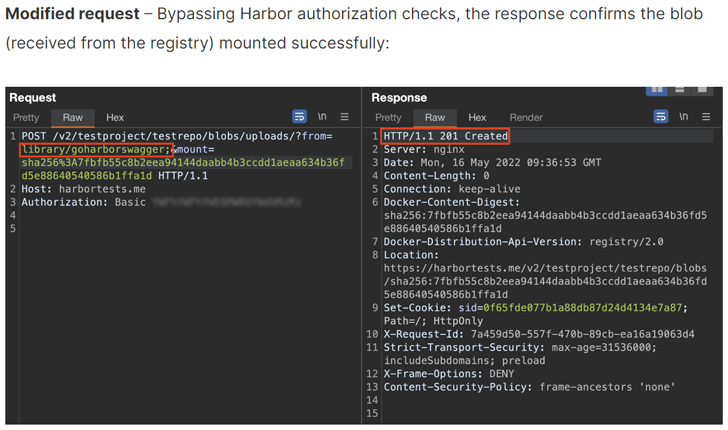
Oxeye said it identified several instances of ParseThru in
open-source projects such as Harbor, Traefik, and Skipper, which
made it possible to bypass validations put in place and carry out
unauthorized actions. The issues have been addressed following
responsible disclosure to the respective vendors.
This is not the first time URL parsing has posed a security
issue. Earlier this January, Claroty and Snyk disclosed[4]
as many as eight flaws in third-party libraries written in C,
JavaScript, PHP, Python, and Ruby languages that originated as a
result of confusion in URL parsing.
References
- ^
report
(www.oxeye.io) - ^
release
notes (go.dev) - ^
one of the methods
(pkg.go.dev) - ^
disclosed
(thehackernews.com)
Read more https://thehackernews.com/2022/08/new-parsethru-parameter-smuggling.html