An enhanced version of the XLoader malware has been spotted
adopting a probability-based approach to camouflage its
command-and-control (C&C) infrastructure, according to the
latest research.
“Now it is significantly harder to separate the wheat from the
chaff and discover the real C&C servers among thousands of
legitimate domains used by Xloader as a smokescreen,” Israeli
cybersecurity company Check Point said[1].
First spotted in the wild in October 2020, XLoader is a
successor to Formbook and a cross-platform information
stealer[2] that’s capable of
plundering credentials from web browsers, capturing keystrokes and
screenshots, and executing arbitrary commands and payloads.
More recently, the ongoing geopolitical conflict[3] between Russia and
Ukraine has proved to be a lucrative fodder for distributing
XLoader[4] by means of phishing emails[5]
aimed at high-ranking government officials in Ukraine.
The latest findings from Check Point build on a previous report
from Zscaler[6]
in January 2022, which revealed the inner workings of the malware’s
C&C (or C2) network encryption and communication protocol,
noting its use of decoy servers to conceal the legitimate server
and evade malware analysis systems.
“The C2 communications occur with the decoy domains and the real
C2 server, including sending stolen data from the victim,” the
researchers explained. “Thus, there is a possibility that a backup
C2 can be hidden in the decoy C2 domains and be used as a fallback
communication channel in the event that the primary C2 domain is
taken down.”
The stealthiness comes from the fact the domain name for the
real C&C server is hidden alongside a configuration containing
64 decoy domains, from which 16 domains are randomly picked,
followed by replacing two of those 16 with the fake C&C address
and the authentic address.
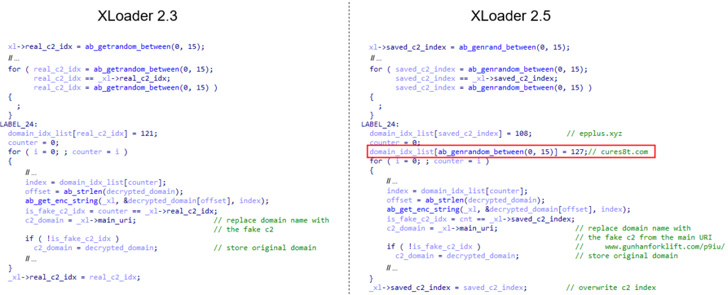
What’s changed in the newer versions of XLoader is that after
the selection of 16 decoy domains from the configuration, the first
eight domains are overwritten with new random values before each
communication cycle while taking steps to skip the real domain.
Additionally, XLoader 2.5 replaces three of the domains in the
created list with two decoy server addresses and the real C&C
server domain. The ultimate goal is to prevent the detection of the
real C&C server, based on the delays between accesses to the
domains.
The fact that the malware authors have resorted to principles of
probability theory[7]
to access the legitimate server once again demonstrates how threat
actors constantly fine-tune their tactics to further their
nefarious goals.
“These modifications achieve two goals at once: each node in the
botnet maintains a steady knockback rate while fooling automated
scripts and preventing the discovery of the real C&C servers,”
Check Point researchers said.
References
- ^
said
(research.checkpoint.com) - ^
cross-platform information stealer
(thehackernews.com) - ^
ongoing
geopolitical conflict (thehackernews.com) - ^
distributing XLoader
(cert.gov.ua) - ^
phishing
emails (www.netskope.com) - ^
Zscaler
(www.zscaler.com) - ^
probability theory
(en.wikipedia.org)
Read more https://thehackernews.com/2022/06/new-xloader-botnet-version-using.html