North Korean regime, has unleashed a new multi-platform malware
framework with an aim to infiltrate corporate entities around the
world, steal customer databases, and distribute ransomware.
Capable of targeting Windows, Linux, and macOS operating
systems, the MATA malware framework — so-called because of the
authors’ reference to the infrastructure as “MataNet” — comes with
a wide range of features designed to carry out a variety of
malicious activities on infected machines.
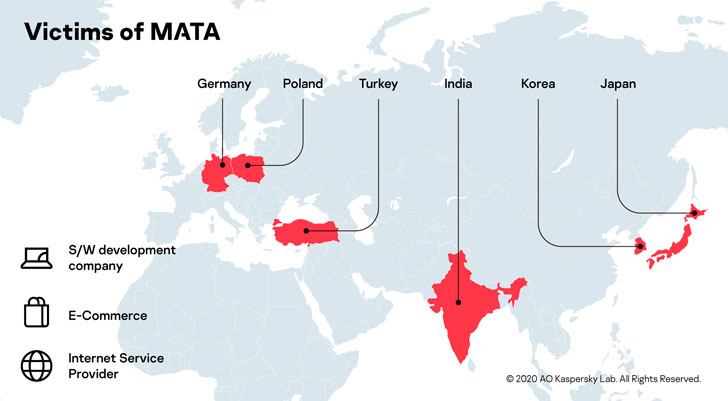
The MATA campaign is said to have begun as early as April of
2018, with the victimology traced to unnamed companies in software
development, e-commerce and internet service provider sectors
situated in Poland, Germany, Turkey, Korea, Japan, and India,
cybersecurity firm Kaspersky said
in its Wednesday analysis.
[1]
The report offers a comprehensive look at the MATA framework, while
also building on previous evidence gathered by researchers from
Netlab 360, Jamf, and Malwarebytes over the past eight months.
Last December, Netlab
360[2] disclosed a fully
functional remote administration Trojan (RAT) called Dacls
targeting both Windows and Linux platforms that shared key
infrastructure with that operated by the Lazarus Group.
Then in May, Jamf[3] and Malwarebytes[4]
uncovered a macOS variant of Dacls RAT that was distributed via a
trojanized two-factor authentication (2FA) app.
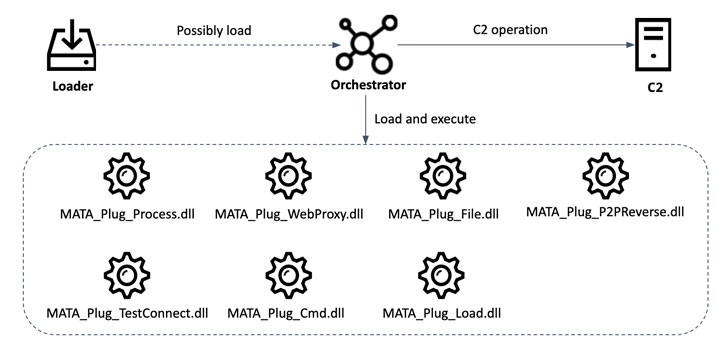
a loader used to load an encrypted next-stage payload — an
orchestrator module (“lsass.exe”) capable of loading 15 additional
plugins at the same time and executing them in memory.
The plugins themselves are feature-rich, boasting features that
allow the malware to manipulate files and system processes, inject
DLLs, and create an HTTP proxy server.
MATA plugins also allow hackers to target Linux-based diskless
network devices such as routers, firewalls or IoT devices, and
macOS systems by masquerading as a 2FA app called TinkaOTP, which
is based on an open-source two-factor authentication application
named MinaOTP.
Once the plugins were deployed, the hackers then tried to locate
the compromised company’s databases and execute several database
queries to acquire customer details. It’s not immediately clear if
they were successful in their attempts. Furthermore, Kaspersky
researchers said MATA was used to distribute VHD ransomware to one
anonymous victim.
Kaspersky said it linked MATA to the Lazarus Group based on the
unique file name format found in the orchestrator (“c_2910.cls” and
“k_3872.cls”), which has been previously seen in several variants
of the Manuscrypt
malware[5].
Cobra[6] or APT38) has been
linked to many major cyber
offensives[7], including the Sony
Pictures hack in 2014, the SWIFT banking hack in 2016, and the
WannaCry
ransomware[8] infection in 2017.
Most recently, the APT added web skimming[9] to their repertoire,
targeting the U.S. and European e-commerce websites to plant
JavaScript-based payment skimmers.
The hacking crew’s penchant for carrying out financially
motivated attacks led the U.S. Treasury to sanction the
group and its two off-shoots, Bluenoroff and Andariel, last
September.
[10]
References
- ^
Kaspersky
(securelist.com) - ^
Netlab 360
(blog.netlab.360.com) - ^
Jamf
(objective-see.com) - ^
Malwarebytes
(blog.malwarebytes.com) - ^
Manuscrypt malware
(us-cert.cisa.gov) - ^
Hidden Cobra
(thehackernews.com) - ^
major cyber offensives
(thehackernews.com) - ^
WannaCry ransomware
(thehackernews.com) - ^
web
skimming (sansec.io) - ^
sanction the group
(thehackernews.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/DVxmjqiYd-s/lazarus-north-korean-hackers.html