A threat with a North Korea nexus has been found leveraging a
“novel spear phish methodology” that involves making use of
trojanized versions of the PuTTY SSH and Telnet client.
Google-owned threat intelligence firm Mandiant attributed the
new campaign to an emerging threat cluster it tracks under the name
UNC4034.
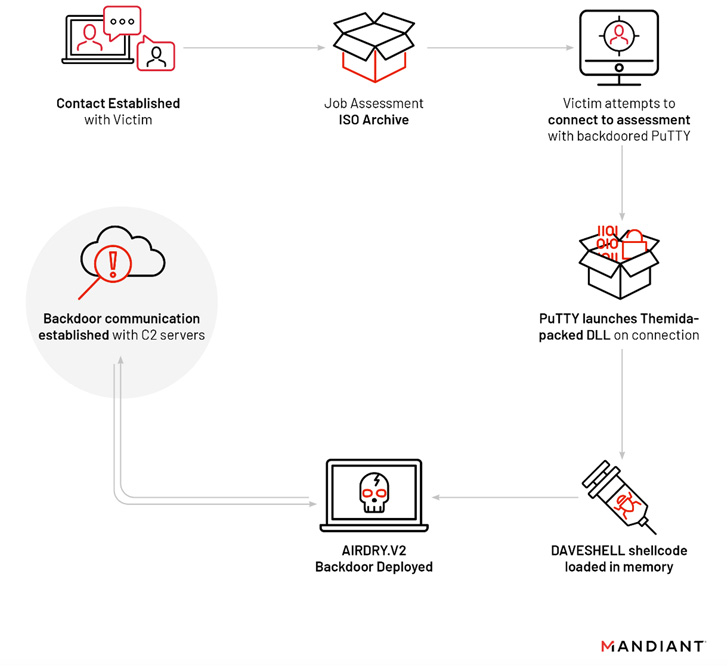
“UNC4034 established communication with the victim over WhatsApp
and lured them to download a malicious ISO package regarding a fake
job offering that led to the deployment of the AIRDRY.V2 backdoor
through a trojanized instance of the PuTTY utility,” Mandiant
researchers said[1].
The use of fabricated job lures as a pathway for malware
distribution is an oft-used tactic by North Korean state-sponsored
actors, including the Lazarus Group, as part of an enduring
campaign called Operation Dream Job[2].
The entry point of the attack is an ISO file that masquerades as
an Amazon Assessment as part of a potential job opportunity at the
tech giant. The file was shared over WhatApp after establishing
initial contact over email.
The archive, for its part, holds a text file containing an IP
address and login credentials, and an altered version of PuTTY
that, in turn, loads a dropper called DAVESHELL, which deploys a
newer variant of a backdoor dubbed AIRDRY.
It’s likely that the threat actor convinced the victim to launch
a PuTTY session and use the credentials provided in the TXT file to
connect to the remote host, effectively activating the
infection.
AIRDRY, also known as BLINDINGCAN, has in the past been used by
North Korea-linked hackers to strike U.S. defense contractors[3] and entities in South Korea and
Latvia[4].
While earlier versions of the malware came with nearly 30
commands for file transfer, file management, and command execution,
the latest version has been found to eschew the command-based
approach in favor of plugins that are downloaded and executed in
memory.
Mandiant said it was able to contain the compromise before any
further post-exploitation activities could take place following the
deployment of the implant.
The development is yet another sign that the use of ISO files
for initial access is gaining traction among threat actors to
deliver both commodity and targeted malware.
The shift is also attributable[5]
to Microsoft’s decision to block Excel 4.0 (XLM or XL4) and Visual
Basic for Applications (VBA) macros for Office apps downloaded from
the internet by default.
References
- ^
said
(www.mandiant.com) - ^
Operation Dream Job
(thehackernews.com) - ^
U.S.
defense contractors (thehackernews.com) - ^
entities
in South Korea and Latvia
(thehackernews.com) - ^
attributable
(thehackernews.com)
Read more https://thehackernews.com/2022/09/north-korean-hackers-spreading.html