Threat actors such as the notorious Lazarus group are continuing
to tap into the ongoing COVID-19 vaccine research to steal
sensitive information to speed up their countries’
vaccine-development efforts.
Cybersecurity firm Kaspersky detailed[1]
two incidents at a pharmaceutical company and a government ministry
in September and October leveraging different tools and techniques
but exhibiting similarities in the post-exploitation process,
leading the researchers to connect the two attacks to the North
Korean government-linked hackers.
“These two incidents reveal the Lazarus group’s interest in
intelligence related to COVID-19,” Seongsu Park, a senior security
researcher at Kaspersky, said. “While the group is mostly known for
its financial activities, it is a good reminder that it can go
after strategic research as well.”
Kaspersky did not name the targeted entities but said the
pharmaceutical firm was breached on September 25, 2020, with the
attack against the government health ministry occurring a month
later, on October 27.
Notably, the incident at the pharmaceutical company — which is
involved in developing and distributing a COVID-19 vaccine — saw
the Lazarus group deploying the “BookCodes[2]” malware, recently used
in a supply-chain attack[3]
of a South Korean software company WIZVERA to install remote
administration tools (RATs) on target systems.
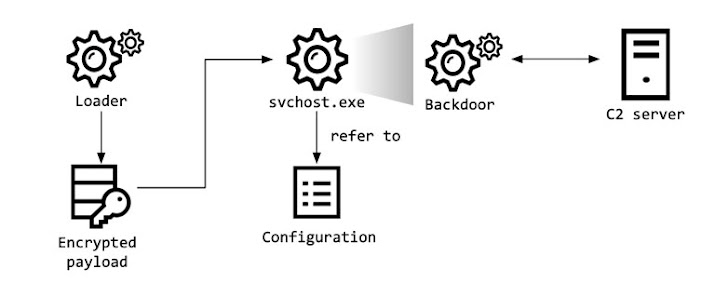
The initial access vector used in the attack remains unknown as
yet, but a malware loader identified by the researchers is said to
load the encrypted BookCodes RAT that comes with capabilities to
collect system information, receive remote commands, and transmit
the results of the execution to command-and-control (C2) servers
located in South Korea.
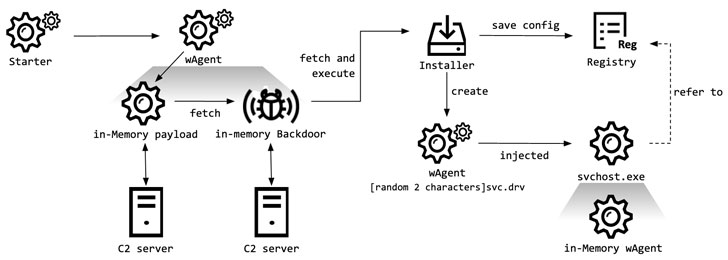
In a separate campaign aimed at the health ministry, the hackers
compromised two Windows servers to install a malware known as
“wAgent,” and then used it to retrieve other malicious payloads
from an attacker-controlled server.
As with the previous case, the researchers said they were unable
to locate the starter module used in the attack but suspect it to
have a “trivial role” of running the malware with specific
parameters, following which wAgent loads a Windows DLL containing
backdoor functionalities directly into memory.
“Using this in-memory backdoor, the malware operator executed
numerous shell commands to gather victim information,” Park
said.
Irrespective of the two malware clusters employed in the
attacks, Kaspersky said the wAgent malware used in October shared
the same infection scheme as the malware that the Lazarus group
used previously in attacks on cryptocurrency businesses, citing
overlaps in the malware naming scheme and debugging messages, and
the use of Security Support Provider as a persistence
mechanism.
The development is the latest in a long list of attacks[4]
capitalizing on the coronavirus pandemic[5]
— a trend observed in various phishing lures and malware campaigns
throughout the last year. North Korean hackers are alleged to have
targeted pharma firms in India, France, Canada, and the UK-based
AstraZeneca.
References
- ^
detailed
(securelist.com) - ^
BookCodes
(www.boho.or.kr) - ^
supply-chain attack
(thehackernews.com) - ^
long
list of attacks (thehackernews.com) - ^
coronavirus pandemic
(thehackernews.com)