An unknown attacker targeted tens of thousands of
unauthenticated Redis servers exposed on the internet in an attempt
to install a cryptocurrency miner[1].
It’s not immediately known if all of these hosts were
successfully compromised. Nonetheless, it was made possible by
means of a “lesser-known technique” designed to trick the servers
into writing data to arbitrary files – a case of unauthorized access[2]
that was first documented in September 2018.
“The general idea behind this exploitation technique is to
configure Redis to write its file-based database to a directory
containing some method to authorize a user (like adding a key to
‘.ssh/authorized_keys’), or start a process (like adding a script
to ‘/etc/cron.d’),” Censys said[3]
in a new write-up.
The attack surface management platform said it uncovered
evidence (i.e., Redis commands) indicating efforts on part of the
attacker to store malicious crontab
entries[4] into the file
“/var/spool/cron/root,” resulting in the execution of a shell
script hosted on a remote server.
The shell script, which is still accessible, is engineered to
perform the following actions –
- Terminate security-related and system monitoring processes
- Purge log files and command histories
- Add a new SSH key (“backup1”) to the root user’s authorized_keys file[5]
to enable remote access - Disable iptables[6]
firewall - Install scanning tools like masscan, and
- Install and run the cryptocurrency mining application
XMRig
The SSH key is said to have been set on 15,526 out of 31,239
unauthenticated Redis servers, suggesting that the attack was
attempted on “over 49% of known unauthenticated Redis servers on
the internet.”
However, a primary reason why this attack could fail is because
the Redis service needs to be running with elevated permissions
(i.e., root) so as to enable the adversary to write to the
aforementioned cron directory.
“Although, this can be the case when running Redis inside a
container (like docker), where the process might see itself running
as root and allow the attacker to write these files,” Censys
researchers said. “But in this case, only the container is
affected, not the physical host.”
Censys’s report also revealed that there are about 350,675
internet-accessible Redis database services spanning 260,534 unique
hosts.
“While most of these services require authentication, 11%
(39,405) do not,” the company said, adding “out of the total 39,405
unauthenticated Redis servers we observed, the potential data
exposure is over 300 gigabytes.”
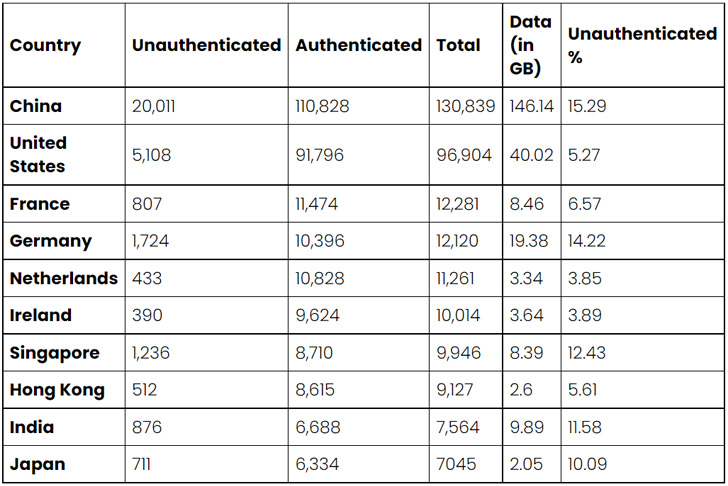
The top 10 countries with exposed and unauthenticated Redis
services include China (20,011), the U.S. (5,108), Germany (1,724),
Singapore (1,236), India (876), France (807), Japan (711), Hong
Kong (512), the Netherlands (433), and Ireland (390).
China also leads when it comes to the amount of data exposed per
country, accounting for 146 gigabytes of data, with the U.S. coming
a distant second with roughly 40 gigabytes.
Censys said it also found numerous instances of Redis services
that have been misconfigured, noting that “Israel is one of the
only regions where the number of misconfigured Redis servers
outnumber the properly configured ones.”
To mitigate threats[7], users are advised to
enable client authentication, configure Redis to run only on
internal-facing network interfaces, prevent the abuse of CONFIG
command by renaming it to something unguessable, and configure
firewalls to accept Redis connections only from trusted hosts.
References
- ^
install
a cryptocurrency miner (thehackernews.com) - ^
unauthorized access
(medium.com) - ^
said
(censys.io) - ^
crontab
entries (en.wikipedia.org) - ^
authorized_keys file
(www.digitalocean.com) - ^
iptables
(en.wikipedia.org) - ^
mitigate
threats (redis.io)
Read more https://thehackernews.com/2022/09/over-39000-unauthenticated-redis.html