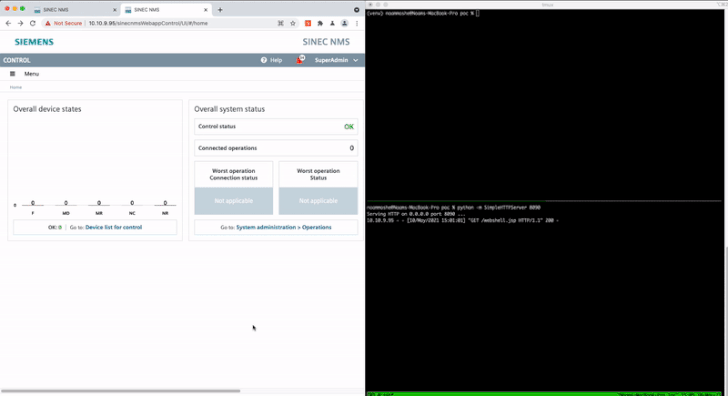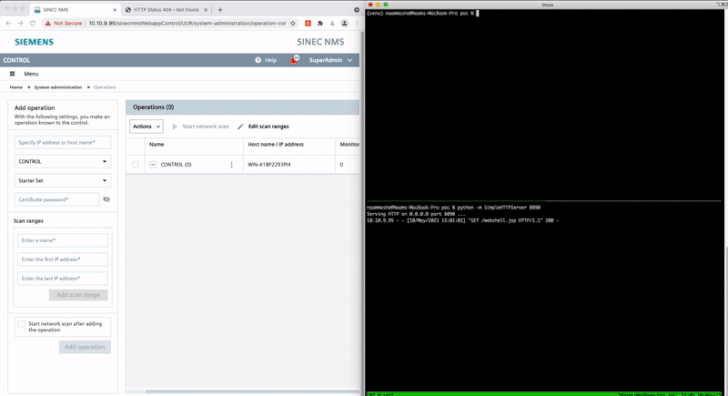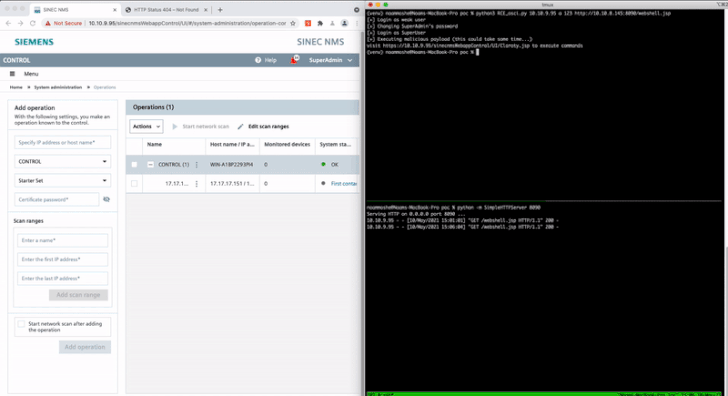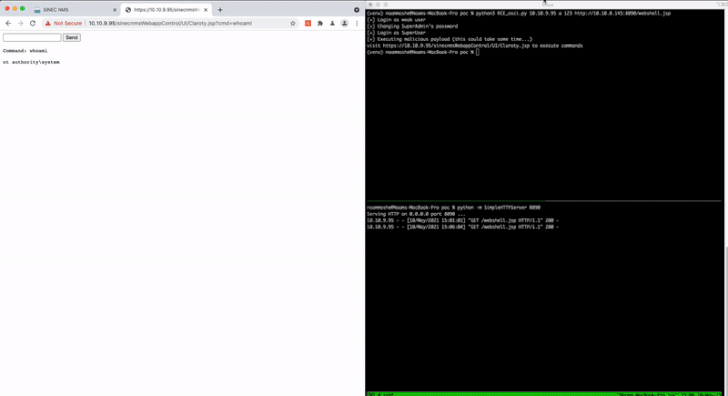
Cybersecurity researchers have disclosed details about 15
security flaws in Siemens SINEC network management system (NMS),
some of which could be chained by an attacker to achieve remote
code execution on affected systems.
“The vulnerabilities, if exploited, pose a number of risks to
Siemens devices on the network including denial-of-service attacks,
credential leaks, and remote code execution in certain
circumstances,” industrial security company Claroty said[1]
in a new report.
The shortcomings in question — tracked from CVE-2021-33722
through CVE-2021-33736 — were addressed by Siemens in version V1.0
SP2 Update 1 as part of updates shipped on October 12, 2021.
“The most severe could allow an authenticated remote attacker to
execute arbitrary code on the system, with system privileges, under
certain conditions,” Siemens noted[2]
in an advisory at the time.
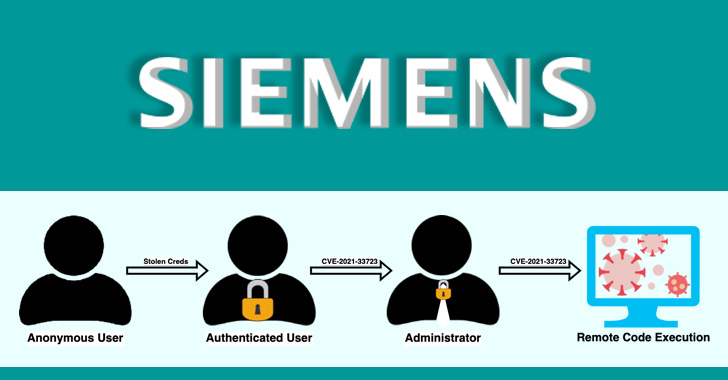
Chief among the weaknesses is CVE-2021-33723 (CVSS score: 8.8),
which allows for privilege escalation to an administrator account
and could be combined with CVE-2021-33722 (CVSS score: 7.2), a path
traversal flaw, to execute arbitrary code remotely.
Another notable flaw relates to a case of SQL injection
(CVE-2021-33729, CVSS score: 8.8) that could be exploited by an
authenticated attacker to execute arbitrary commands in the local
database.
“SINEC is in a powerful central position within the network
topology because it requires access to the credentials,
cryptographic keys, and other secrets granting it administrator
access in order to manage devices in the network,” Claroty’s Noam
Moshe said.
“From an attacker’s perspective carrying out a
living-off-the-land type of attack where legitimate credentials and
network tools are abused to carry out malicious activity, access
to, and control of, SINEC puts an attacker in prime position for:
reconnaissance, lateral movement, and privilege escalation.”
Read more https://thehackernews.com/2022/06/over-dozen-flaws-found-in-siemens.html