modern DRAM (dynamic random access memory) chips that could allow
attackers to obtain higher kernel privileges on a targeted system
by repeatedly accessing memory cells and induce bit flips.
To mitigate Rowhammer
vulnerability on the latest DDR4 DRAM, many memory chip
manufacturers added some defenses under the umbrella term Target
Row Refresh (TRR) that refreshes adjacent rows when a victim
row is accessed more than a threshold.
[1]
But it turns out ‘Target Row Refresh,’ promoted as a silver bullet
to mitigate rowhammer attacks, is also insufficient and could let
attackers execute new hammering patterns and re-enable the bit-flip
attacks on the latest hardware as well.
TRRespass: The Rowhammer Fuzzing Tool
Tracked as CVE-2020-10255, the newly reported[2]
vulnerability was discovered by researchers at VUSec Lab, who today
also released ‘TRRespass,’ an open source black box
many-sided RowHammer fuzzing tool[3]
that can identify sophisticated hammering patterns to mount
real-world attacks.
According to the researchers, TRRespass fuzzer repeatedly
selects different random rows at various locations in DRAM for
hammering and works even when unaware of the implementation of the
memory controller or the DRAM chip.
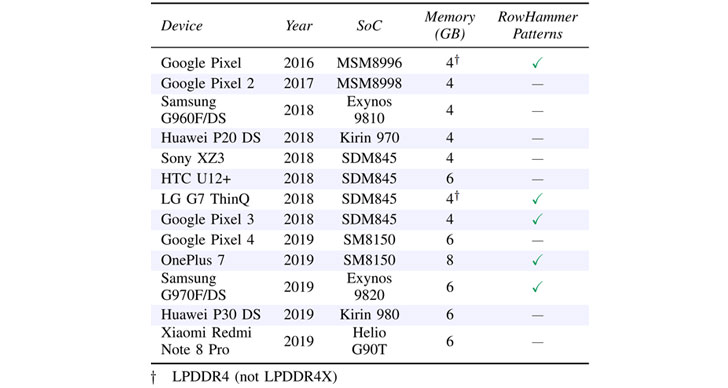
What’s more? The latest flaw also affects LPDDR4 and
LPDDR4X chips embedded on most of the modern smartphones[4], leaving millions of
devices still vulnerable to the RowHammer
vulnerability[5]
again.
managed to trigger bit flips on a variety of smartphones such as
Google Pixel 3 and Samsung Galaxy S10,” the researchers said.
Target Row Refresh tries to identify possible victim rows by
counting the number of adjacent row activations and comparing it
against a predefined value, but it still is incapable of keeping
the information about all accessed rows at the same time to
effectively mitigate bit flips through aggressor rows.
“The known Rowhammer variants use at most two aggressor rows to
perform the attack, a small number rows that are being accessed
frequently can easily be monitored by TRR. But what if we use more
aggressor rows?” the researchers said in a blog post.
“But having more aggressors overwhelms the TRR mitigation since
it can only track a few aggressor rows at a time. ‘Luckily’ DDR4
chips are more vulnerable, giving us the possibility to reduce the
number of accesses to each of the aggressors to trigger bit flips.
Or, in other words, to increase the number of aggressors to bypass
the mitigation.”
Researchers claim they “tried TRRespass on the three major
memory vendors (compromising more than 99% of the market) using 42
DIMMs,” and found bit flips on 12 of them.
VUSec team reported the new RowHammer attacks to all affected
parties late last year, but, unfortunately, it is not going to be
patched anytime soon.
VUSec also promised to soon release an Android app that users
can install and use to check whether the memory chip on their
smartphones is also vulnerable to the new hammering patterns or
not.
References
- ^
Rowhammer vulnerability
(thehackernews.com) - ^
reported
(www.vusec.net) - ^
RowHammer fuzzing tool
(github.com) - ^
smartphones
(thehackernews.com) - ^
RowHammer vulnerability
(thehackernews.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/JXhRsG7hUy8/rowhammer-vulnerability-ddr4-dram.html