Taiwanese company QNAP has warned customers to secure
network-attached storage (NAS) appliances and routers against a new
ransomware variant called DeadBolt.
“DeadBolt has been widely targeting all NAS exposed to the
Internet without any protection and encrypting users’ data for
Bitcoin ransom,” the company said[1]. “QNAP urges all QNAP
NAS users to […] immediately update QTS to the latest available
version.”
In addition, QNAP is also urging users to check if their NAS
devices are public-facing, and if so, take steps to turn off the
port forwarding function of the router and disable the Universal
Plug and Play (UPnP[2]) function of the QNAP
NAS.
The advisory comes as Bleeping Computer[3]
revealed that QNAP NAS devices are being encrypted by the DeadBolt
ransomware by exploiting a supposed zero-day vulnerability in the
device’s software. The attacks are believed to have started on
January 25.
The ransomware strain, which locks the files[4]
with a “.deadbolt” file extension, demands that victims pay a
ransom of 0.03 bitcoins (approximately $1,100) to a unique Bitcoin
address in exchange for a decryption key.
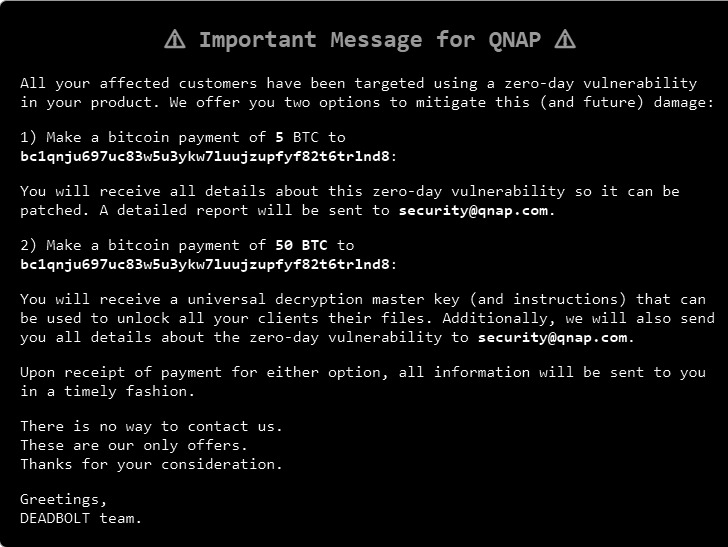
On top of that, the operators of the ransomware claimed[5]
they are willing to offer complete details of the alleged zero-day
flaw if QNAP pays them five bitcoins (~$186,700). It’s also ready
to sell the master decryption key that can be used to unlock the
files for all affected victims for an extra 45 bitcoins (~$1.7
million).
While it’s not immediately clear if QNAP heeded to the extortion
demand, the company, on Reddit, acknowledged[6]
that it had silently force-installed an emergency firmware update
to “increase protection” against the ransomware, adding “It is a
hard decision to make. But it is because of DeadBolt and our desire
to stop this attack as soon as possible that we did this.”
QNAP devices have emerged a frequent target of ransomware groups[7]
and other criminal actors[8], prompting the company
to issue numerous warnings in recent months. On January 7, it
advised[9]
customers to safeguard their NAS devices from ransomware and
brute-force attacks, and ensure that they are not exposed to the
internet.
We have reached out to QNAP for further comment, and we’ll
update the story if we hear back.
References
- ^
said
(www.qnap.com) - ^
UPnP
(en.wikipedia.org) - ^
Bleeping
Computer (www.bleepingcomputer.com) - ^
locks
the files (forum.qnap.com) - ^
claimed
(twitter.com) - ^
acknowledged
(www.reddit.com) - ^
ransomware groups
(thehackernews.com) - ^
criminal
actors (thehackernews.com) - ^
advised
(www.qnap.com)
Read more https://thehackernews.com/2022/01/qnap-warns-of-deadbolt-ransomware.html