joint advisory about a massive ongoing malware
threat infecting Taiwanese company QNAP’s network-attached storage
(NAS) appliances.
Called QSnatch (or Derek), the data-stealing malware is said to
have compromised 62,000 devices since reports emerged last October,
with a high degree of infection in Western Europe and North
America.
“All QNAP NAS devices are potentially vulnerable to QSnatch
malware if not updated with the latest security fixes,” the US
Cybersecurity and Infrastructure Security Agency (CISA) and the
UK’s National Cyber Security Centre (NCSC) said in the alert.
“Further, once a device has been infected, attackers can prevent
administrators from successfully running firmware updates.”
The mode of compromise, i.e., the infection vector, still remains
unclear, but CISA and NCSC said the first campaign likely began in
2014 and continued till mid-2017 before intensifying over the last
few months to infect about 7,600 devices in the US and
approximately 3,900 devices in the UK.
Over 7,000 NAS devices[3] were targeted with the
malware in Germany alone, according to the German Computer
Emergency Response Team (CERT-Bund) as of October 2019.
Although the infrastructure used by the bad actors in both
campaigns is not currently active, the second wave of attacks
involves injecting the malware during the infection stage and
subsequently using a domain generation algorithm (DGA[4]) to set up a
command-and-control (C2) channel for remote communication with the
infected hosts and exfiltrate sensitive data.
well as some differences in capabilities,” the agencies said.
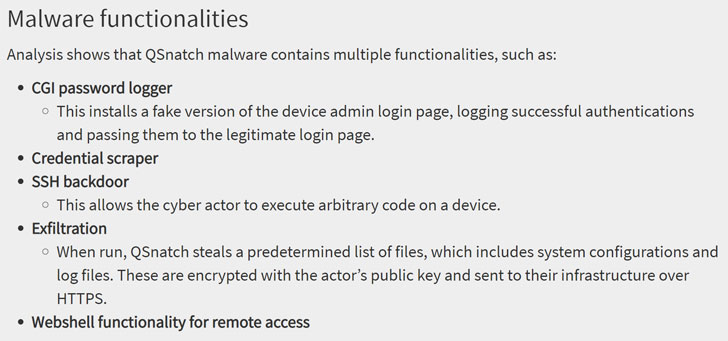
The latest version of QSnatch comes with a broad range of
features, including a CGI password logger that uses a fake admin
login screen to capture passwords, a credential scraper, an SSH
backdoor capable of executing arbitrary code, and a web shell
functionality to access the device remotely.
In addition, the malware gains persistence by preventing updates
from getting installed on the infected QNAP device, which is done
by “redirecting core domain names used by the NAS to local
out-of-date versions so updates can never be installed.”
The two agencies have urged organizations to ensure their
devices have not been previously compromised, and if so, run a full
factory reset on the device before performing the firmware upgrade.
It’s also recommended to follow QNAP’s security advisory to prevent
the infection by following the steps listed here[5].
“Verify that you purchased QNAP devices from reputable sources,”
CISA and NCSC suggested as part of additional mitigation against
QSnatch. “Block external connections when the device is intended to
be used strictly for internal storage.”
References
- ^
joint
(us-cert.cisa.gov) - ^
advisory
(www.ncsc.gov.uk) - ^
7,000 NAS devices
(twitter.com) - ^
DGA
(en.wikipedia.org) - ^
steps listed here
(www.qnap.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/e35LebcDVDQ/qnap-nas-malware-attack.html