unpatched weakness in Microsoft’s Azure cloud service by exploiting
it to take control over Windows Live Tiles, one of the key
features Microsoft built into Windows 8 operating system.
Introduced in Windows 8, the Live tiles feature was designed to
display content and notifications on the Start screen, allowing
users to continuously pull up-to-date information from their
favorite apps and websites.
To make it easier for websites to offer their content as Live
Tiles, Microsoft had a feature available on a subdomain of a
separate domain, i.e.,
“notifications.buildmypinnedsite.com,” that allowed website
admins to automatically convert their RSS feeds into a special XML
format and use it as a meta tag on their websites.
The service, which Microsoft had already shut down, was hosted on
its own Azure Cloud platform with the subdomain configured/linked
to an Azure account operated by the company.
However, it turns out that even after disabling the RSS-to-XML
converter service, the company forgot to delete nameserver entries,
leaving the unclaimed subdomain still pointing to the Azure
servers.
Hanno Böck, who discovered this
issue, seized this opportunity to exploit the weakness and
reclaimed the same subdomain using a newly created account on
Azure.
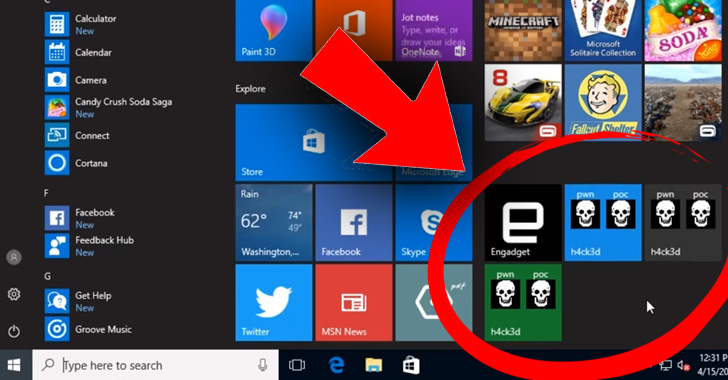
[1]
made it possible for him to push arbitrary content or notifications
on Windows Live Tiles of various app or websites that are still
using meta tags generated by the disabled service.
“With an ordinary Azure account, we were able to register that
subdomain and add the corresponding hostname. Thus we were able to
control which content is served on that host,” Böck said.
“Web pages that contain these meta tags should remove them or if
they want to keep the functionality, create the appropriate XML
files themselves.”
important attack vector that can usually be found in the way most
online services allow their users to run web apps or blogs with a
custom domain name.
For example, when you create an app on Azure and wants to make it
available on the Internet with a custom domain name, the platform
asks users to point their domain’s nameserver to Azure and then
claim it within their account’s dashboard, without verifying the
domain ownership.
Since Microsoft Azure does not have a mechanism to verify if the
account claiming a domain really owns it, any Azure user can claim
any unclaimed domain (or left unattended) that have nameservers
pointing to the cloud service.
“We have informed about this problem but have not received it yet,”
Böck said. “Once we cancel the subdomain a bad actor could register
it and abuse it for malicious attacks.”
company patched a few years ago by making it mandatory for every
blog owner to set a separate, unique TXT record for their custom
domains in order to verify the claim.
Though it seems Microsoft has now secured its subdomain by
removing the nameservers, The Hacker News reached out to Microsoft
to learn if the company has any plans to fix the “subdomain
takeover” issue in its Azure cloud service platform that could
eventually affect other domain users as well.
We will update this report when we hear back.
References
- ^
discovered
(www.golem.de)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/ua7YL1rpNME/subdomain-microsoft-azure.html