As ransomware infections have evolved from purely encrypting
data to schemes such as double and triple extortion, a new attack
vector is likely to set the stage for future campaigns.
Called Ransomware for IoT or R4IoT[1]
by Forescout, it’s a “novel, proof-of-concept ransomware that
exploits an IoT device to gain access and move laterally in an IT
[information technology] network and impact the OT [operational
technology] network.”
This potential pivot is based on the rapid growth in the number
of IoT devices as well as the convergence of IT and OT networks in
organizations.
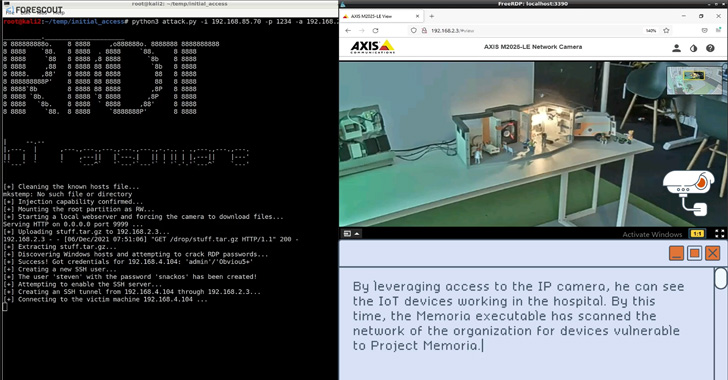
The ultimate goal of R4IoT is to leverage exposed and vulnerable
IoT devices such as IP cameras to gain an initial foothold,
followed by deploying ransomware in the IT network and taking
advantage of poor operational security practices to hold
mission-critical processes hostage.
“By compromising IoT, IT, and OT assets, R4IoT goes beyond the
usual encryption and data exfiltration to cause physical disruption
of business operations,” the researchers said, thereby adding an
additional layer of extortion to a traditional ransomware
attack.
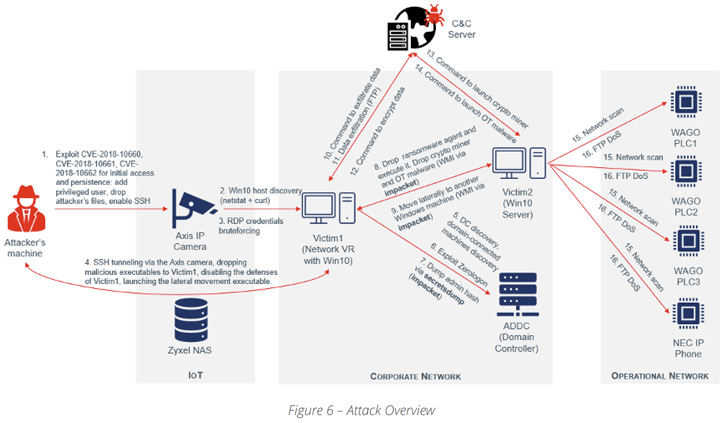
Put differently, R4IoT is a new kind of malware that brings
together an IoT entry point and ransomware-related lateral movement
and encryption on an IT network, causing an extended impact on both
IT and OT networks.
In a hypothetical scenario, this could entail compromising a
machine in the corporate network to not only drop ransomware but
also retrieve additional payloads from a remote server to deploy
cryptocurrency miners and launch denial-of-service (DoS) attacks
against OT assets.
To mitigate both the likelihood and the impact of potential
R4IoT incidents, organizations are recommended to identify and
patch vulnerable devices, enforce network segmentation, implement
strong password policies, and monitor HTTPS connections, FTP
sessions, and network traffic.
“Ransomware has been the most prevalent threat of the past few
years, and so far, it has mostly leveraged vulnerabilities in
traditional IT equipment to cripple organizations,” the researchers
concluded.
“But new connectivity trends have added a number and a diversity
of OT and IoT devices that have increased risk in nearly every
business.”
Read more https://thehackernews.com/2022/06/researchers-demonstrate-ransomware-for.html