A new piece of research has detailed the increasingly
sophisticated nature of the malware toolset employed by an advanced
persistent threat (APT) group named Earth Aughisky.
“Over the last decade, the group has continued to make
adjustments in the tools and malware deployments on specific
targets located in Taiwan and, more recently, Japan,” Trend Micro
disclosed[1]
in a technical profile last week.
Earth Aughisky, also known as Taidoor[2], is a cyber espionage
group that’s known for its ability to abuse legitimate accounts,
software, applications, and other weaknesses in the network design
and infrastructure for its own ends.
While the Chinese threat actor has been known to primarily
target organizations in Taiwan, victimology patterns observed
towards late 2017 indicate an expansion to Japan.
The most commonly targeted industry verticals include
government, telcom, manufacturing, heavy, technology,
transportation, and healthcare.
Attack chains mounted by the group typically leverage
spear-phishing as a method of entry, using it to deploy next-stage
backdoors. Chief among its tools is a remote access trojan called
Taidoor[3]
(aka Roudan).
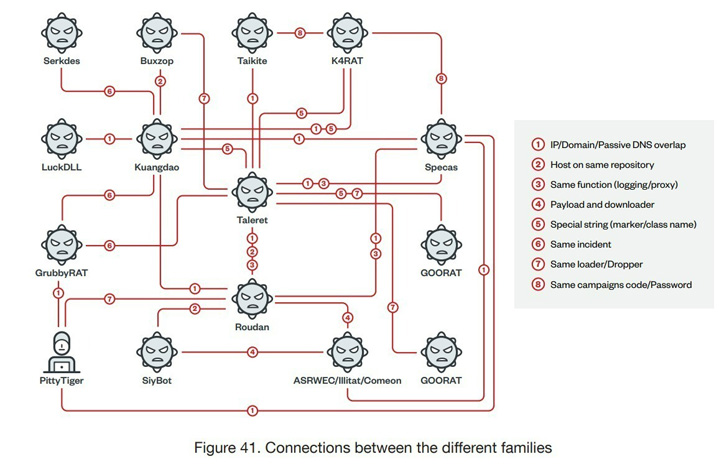
The group has also been linked to a variety of malware families,
such as GrubbyRAT, K4RAT, LuckDLL, Serkdes, Taikite, and Taleret,
as part of its attempts to consistently update its arsenal to evade
security software.
Some of the other notable backdoors employed by Earth Aughisky
over the years are as follows –
- SiyBot, a basic backdoor that uses public services like Gubb
and 30 Boxes for command-and-control (C2) - TWTRAT, which abuses Twitter’s direct message feature for
C2 - DropNetClient (aka Buxzop), which leverages the Dropbox API for
C2
Trend Micro’s attribution of the malware strains to the threat
actor is based on the similarities in source code, domains, and
naming conventions, with the analysis also uncovering functional
overlaps between them.
The cybersecurity firm also linked the activities of Earth
Aughisky to another APT actor codenamed by Airbus as Pitty Tiger[4]
(aka APT24[5]) owing to the use of the
same dropper in various attacks that transpired between April and
August 2014.
2017, the year when the group set its sights on Japan and
Southeast Asia, has also been an inflection point in the way the
volume of the attacks has exhibited a significant decline since
then.
Despite the longevity of the threat actor, the recent shift in
targets and activities likely suggests a change in strategic
objectives or that the group is actively revamping its malware and
infrastructure.
“Groups like Earth Aughisky have sufficient resources at their
disposal that allow them the flexibility to match their arsenal for
long-term implementations of cyber espionage,” Trend Micro
researcher CH Lei said.
“Organizations should consider this observed downtime from this
group’s attacks as a period for preparation and vigilance for when
it becomes active again.”
References
Read more https://thehackernews.com/2022/10/researchers-detail-malicious-tools-used.html