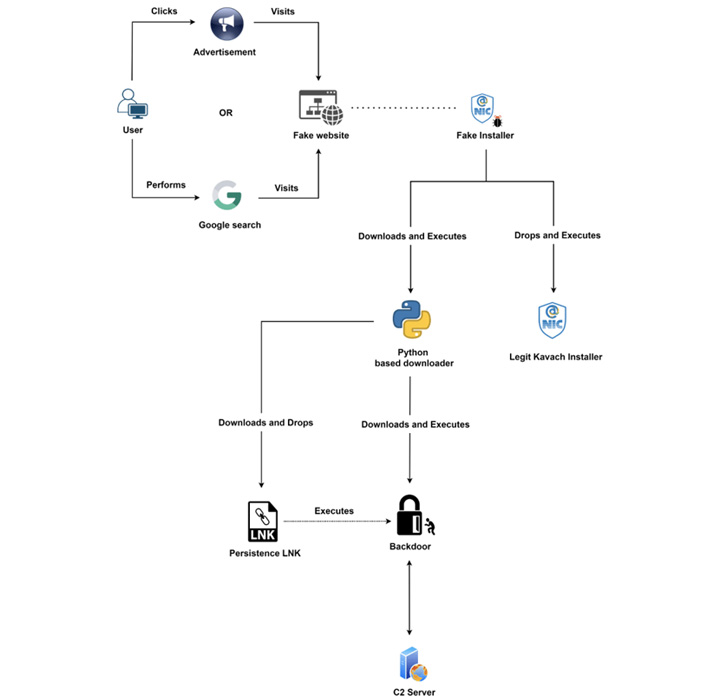
The Transparent Tribe threat actor has been linked to a new
campaign aimed at Indian government organizations with trojanized
versions of a two-factor authentication solution called
Kavach.
“This group abuses Google advertisements for the purpose of
malvertising to distribute backdoored versions of Kavach
multi-authentication (MFA) applications,” Zscaler ThreatLabz
researcher Sudeep Singh said[1]
in a Thursday analysis.
The cybersecurity company said the advanced persistent threat
group has also conducted low-volume credential harvesting attacks
in which rogue websites masquerading as official Indian government
websites were set up to lure unwitting users into entering their
passwords.
Transparent Tribe, also known by the monikers APT36, Operation
C-Major, and Mythic Leopard, is a suspected Pakistan adversarial collective[2]
that has a history[3]
of striking Indian and Afghanistan entities.
The latest attack chain is not the first time the threat actor
has set its sights on Kavach (meaning “armor” in Hindi), a mandatory app[4]
required by users with email addresses on the @gov.in and @nic.in
domains to sign in to the email service as a second layer of
authentication.
Earlier this March, Cisco Talos uncovered[5]
a hacking campaign that employed fake Windows installers for Kavach
as a decoy to infect government personnel with CrimsonRAT and other
artifacts.
One of their common tactics is the mimicking of legitimate
government, military, and related organizations to activate the
killchain. The latest campaign conducted by the threat actor is no
exception.
“The threat actor registered multiple new domains hosting web
pages masquerading as the official Kavach app download portal,”
Singh said. “They abused the Google Ads’ paid search feature to
push the malicious domains to the top of Google search results for
users in India.”
Since May 2022, Transparent Tribe is also said to have
distributed backdoored versions of the Kavach app through
attacker-controlled application stores that claim to offer free
software downloads.
This website is also surfaced as a top result in Google
searches, effectively acting as a gateway to redirect users looking
for the app to the .NET-based fraudulent installer.
The group, beginning August 2022, has also been observed using a
previously undocumented data exfiltration tool codenamed LimePad,
which is designed to upload files of interest from the infected
host to the attacker’s server.
Zscaler said it also identified a domain registered by
Transparent Tribe spoofing the login page of the Kavach app[6] that was only displayed
accessed from an Indian IP address, or else redirected the visitor
to the home page of India’s National Informatics Centre (NIC[7]).
The page, for its part, is equipped to capture the credentials
entered by the victim and send them to a remote server for carrying
out further attacks against government-related infrastructure.
The use of Google ads and LimePad points to the threat actor’s
continued attempts at evolving and refining its tactics and malware
toolset.
“APT-36 continues to be one of the most prevalent advanced
persistent threat groups focused on targeting users working in
Indian governmental organizations,” Singh said. “Applications used
internally at the Indian government organizations are a popular
choice of social engineering theme used by the APT-36 group.”
References
- ^
said
(www.zscaler.com) - ^
adversarial collective
(thehackernews.com) - ^
history
(thehackernews.com) - ^
mandatory app
(dot.gov.in) - ^
uncovered
(thehackernews.com) - ^
login
page of the Kavach app (kavach.mail.gov.in) - ^
NIC
(www.nic.in)
Read more https://thehackernews.com/2022/11/researchers-detail-new-malware-campaign.html