Cybersecurity researchers have disclosed details about a pair of
vulnerabilities in Microsoft Windows, one of which could be
exploited to result in a denial-of-service (DoS).
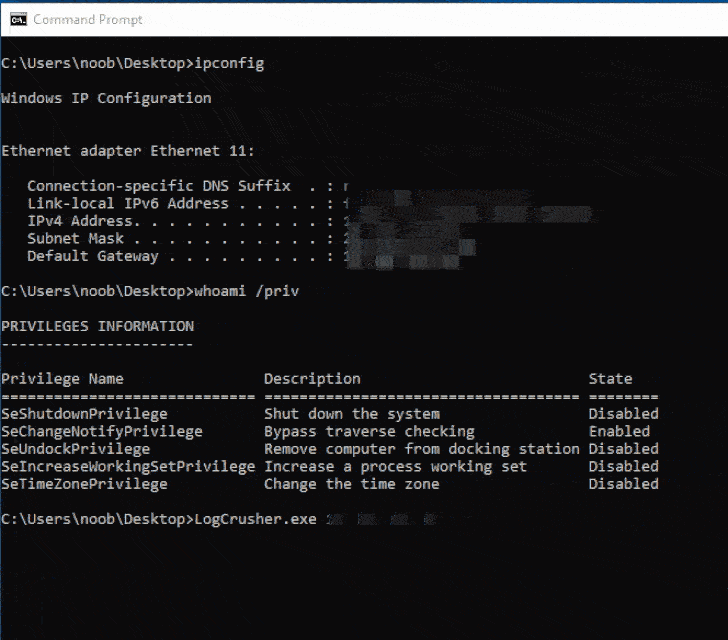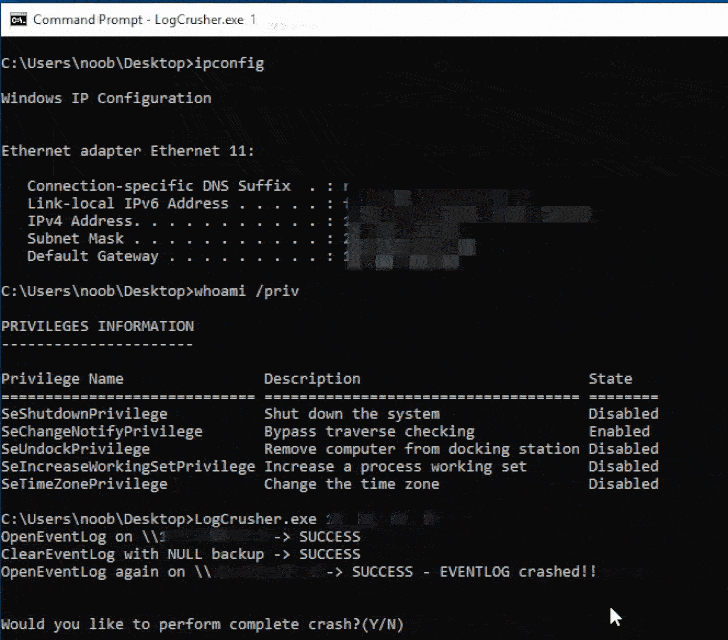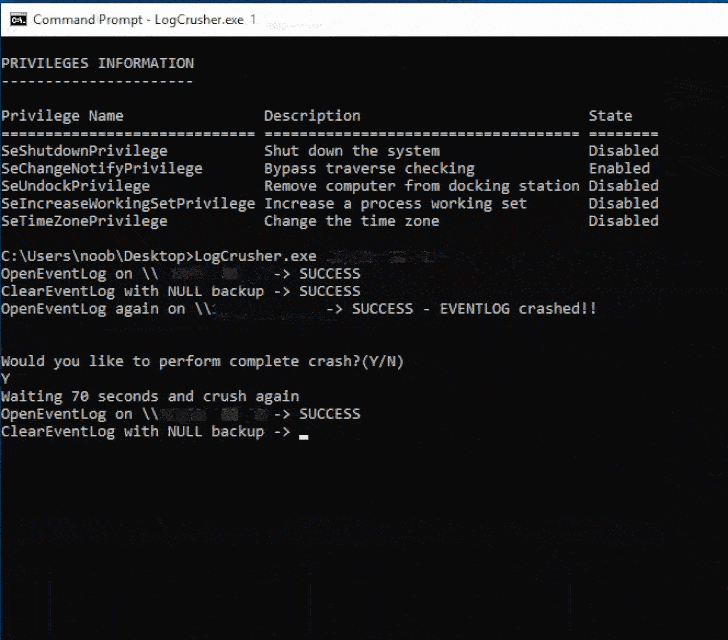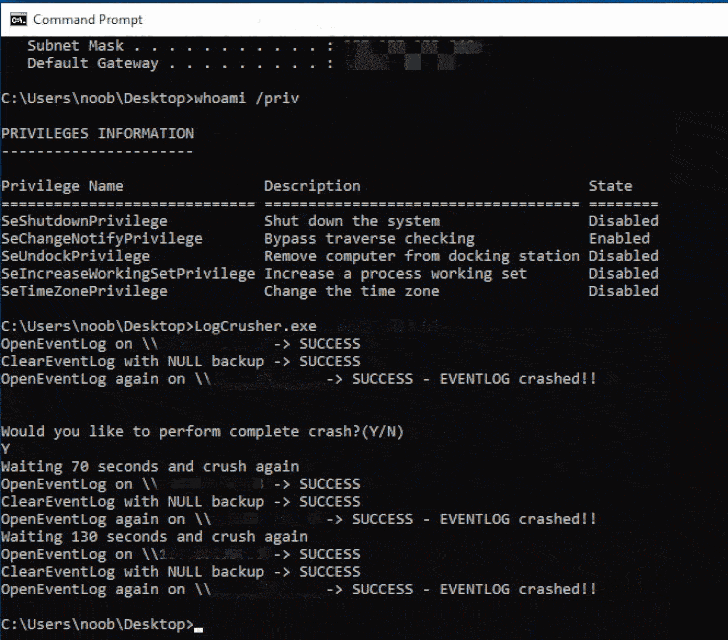
The exploits, dubbed LogCrusher and
OverLog by Varonis, take aim at the EventLog
Remoting Protocol (MS-EVEN[1]), which enables remote
access to event logs.
While the former allows “any domain user to remotely crash the
Event Log application of any Windows machine,” OverLog causes a DoS
by “filling the hard drive space of any Windows machine on the
domain,” Dolev Taler said[2]
in a report shared with The Hacker News.
OverLog has been assigned the CVE identifier CVE-2022-37981
(CVSS score: 4.3) and was addressed by Microsoft as part of its
October Patch Tuesday[3]
updates. LogCrusher, however, remains unresolved.
“The performance can be interrupted and/or reduced, but the
attacker cannot fully deny service,” the tech giant said in an
advisory for the flaw released earlier this month.
The issues, according to Varonis, bank on the fact that an
attacker can obtain a handle to the legacy Internet Explorer log,
effectively setting the stage for attacks that leverage the handle
to crash the Event Log on the victim machine and even induce a DoS
condition.
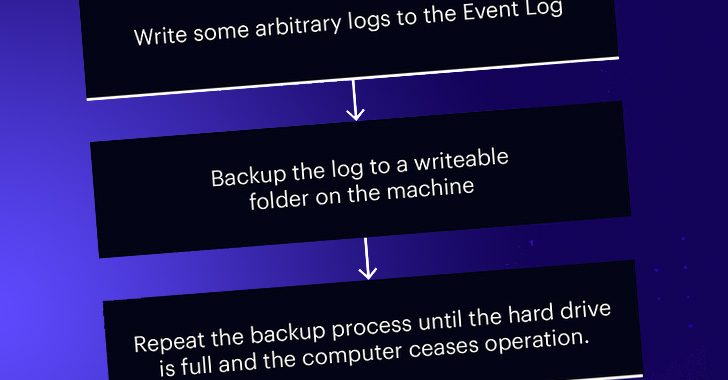
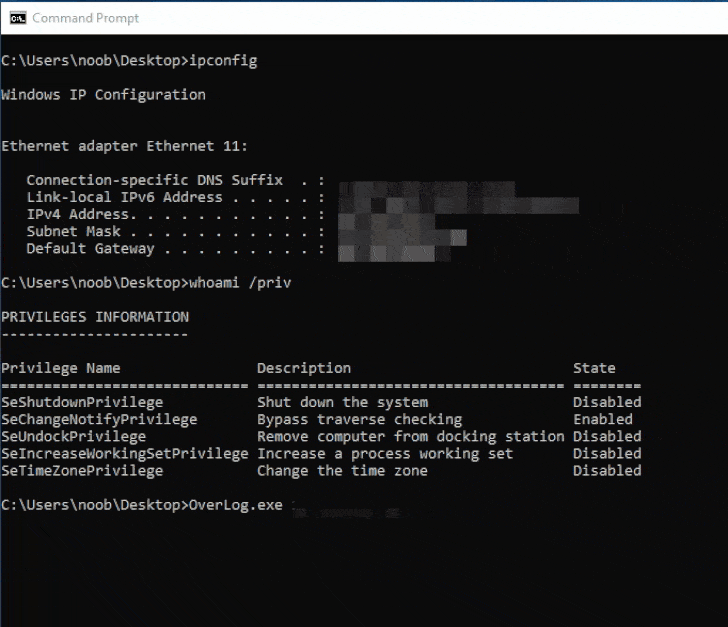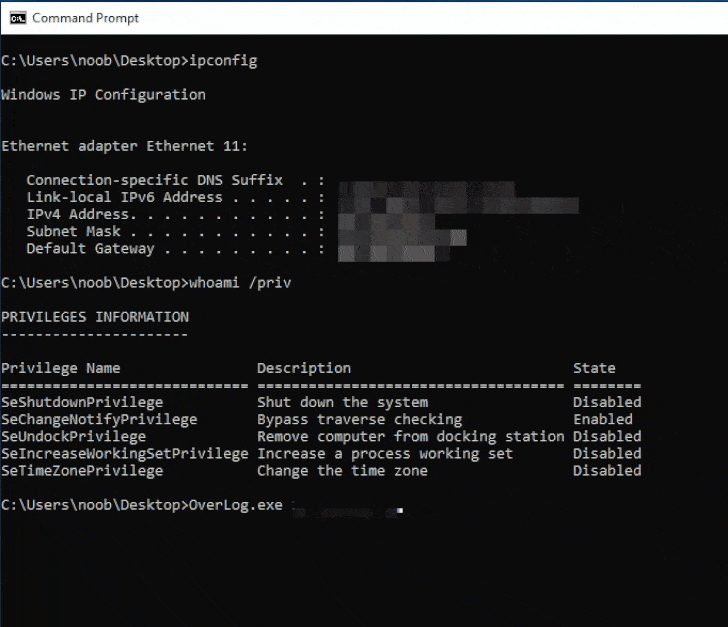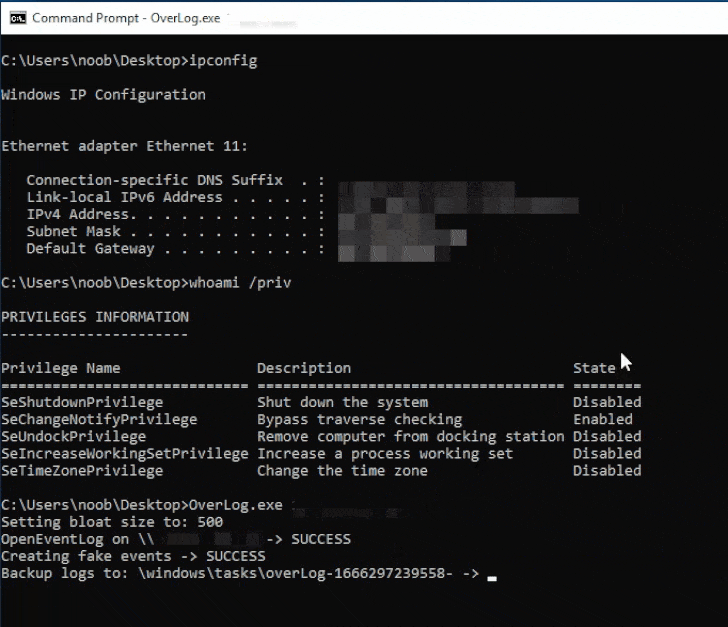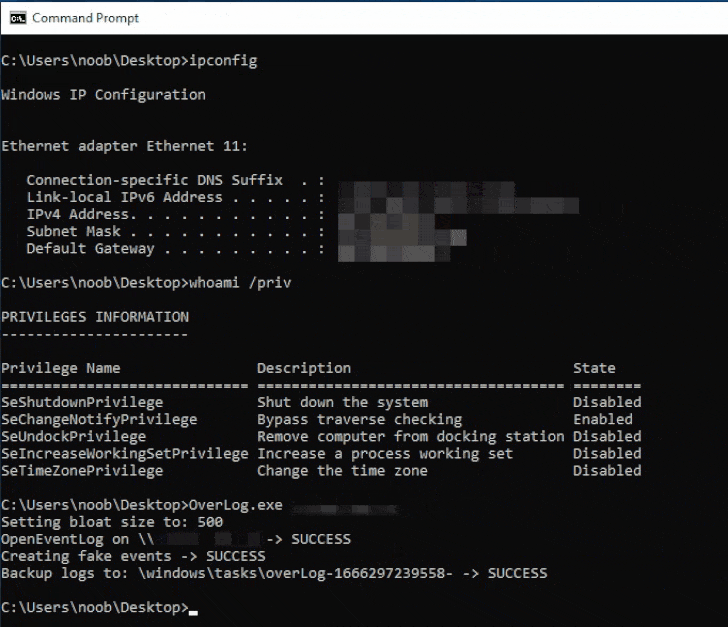
This is achieved by combining it with another flaw in a log
backup function (BackupEventLogW[4]) to repeatedly backup
arbitrary logs to a writable folder on the targeted host until the
hard drive gets filled.
Microsoft has since remediated the OverLog flaw by restricting
access to the Internet Explorer Event Log to local administrators,
thereby reducing the potential for misuse.
“While this addresses this particular set of Internet Explorer
Event Log exploits, there remains potential for other
user-accessible application Event Logs to be similarly leveraged
for attacks,” Taler said.
References
- ^
MS-EVEN
(learn.microsoft.com) - ^
said
(www.varonis.com) - ^
October
Patch Tuesday (thehackernews.com) - ^
BackupEventLogW
(learn.microsoft.com)
Read more https://thehackernews.com/2022/10/researchers-detail-windows-event-log.html