botnet-driven spam campaigns and ransomware attacks, contained a
flaw that allowed cybersecurity researchers to activate a
kill-switch and prevent the malware from infecting systems for six
months.
“Most of the vulnerabilities and exploits that you read about
are good news for attackers and bad news for the rest of us,”
Binary Defense’s James
Quinn[1] said.
“However, it’s important to keep in mind that malware is
software that can also have flaws. Just as attackers can exploit
flaws in legitimate software to cause harm, defenders can also
reverse-engineer malware to discover its vulnerabilities and then
exploit those to defeat the malware.”
The kill-switch was alive between February 6, 2020, to August 6,
2020, for 182 days, before the malware authors patched their
malware and closed the vulnerability.
initial roots as a banking malware to a “Swiss Army knife” that can
serve as a downloader, information stealer, and spambot depending
on how it’s deployed.
Early this February, it developed a new
featur[2]e to leverage already
infected devices to identify and compromise fresh victims connected
to nearby Wi-Fi networks.
Along with this feature update came a new persistence mechanism,
according to Binary Defense, which “generated a filename to save
the malware on each victim system, using a randomly chosen exe or
dll system filename from the system32 directory.”
The change in itself was straight-forward: it encrypted the
filename with an XOR key that was then saved to the Windows
registry value set to the victim’s volume serial number.
The first version of the kill-switch developed by Binary
Defense, which went live about 37 hours after Emotet unveiled the
above changes, employed a PowerShell script that would generate the
registry key value for each victim and set the data for each value
to null.
it would end up loading an empty exe “.exe,” thus stopping the
malware from running on the target system.
“When the malware attempts to execute ‘.exe,’ it would be unable
to run because ‘.’ translates to the current working directory for
many operating systems,” Quinn noted.
EmoCrash to Thwart Emotet
That’s not all. In an improvised version of the kill-switch, called
EmoCrash, Quinn said he was able to exploit a buffer overflow
vulnerability discovered in the malware’s installation routine to
crash Emotet during the installation process, thereby effectively
preventing users from getting infected.
So instead of resetting the registry value, the script works by
identifying the system architecture to generate the install
registry value for the user’s volume serial number, using it to
save a buffer of 832 bytes.
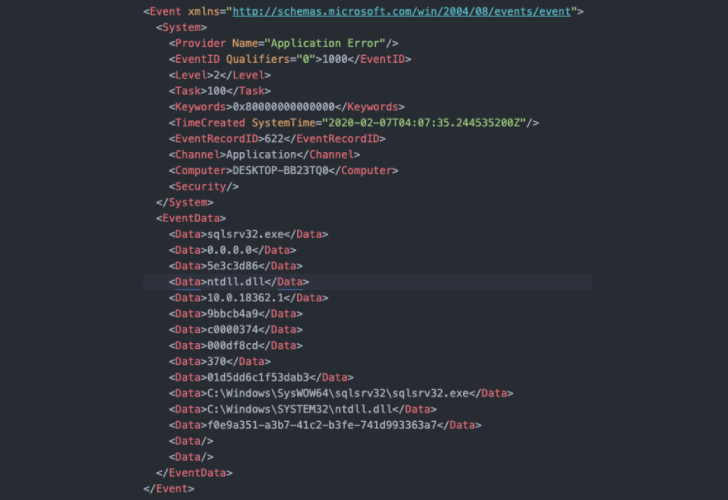
“This tiny data buffer was all that was needed to crash Emotet,
and could even be deployed prior to infection (like a vaccine) or
mid-infection (like a killswitch),” Quinn said. “Two crash logs
would appear with event ID 1000 and 1001, which could be used to
identify endpoints with disabled and dead Emotet binaries after
deployment of the killswitch (and a computer restart).”
To keep it a secret from threat actors and patch their code,
Binary Defense said it coordinated with Computer Emergency Response
Teams (CERTs) and Team Cymru to distribute the EmoCrash exploit
script to susceptible organizations.
Although Emotet retired its registry key-based installation
method in mid-April, it wasn’t until August 6 when an update to the
malware loader entirely removed the vulnerable registry value
code.
“On July 17, 2020, Emotet finally returned to spamming after
their several months-long development period,” Quinn said. “With
EmoCrash still active at the start of their full return, up until
August 6, EmoCrash was able to provide total protection from
Emotet.”
“Not bad for a 832-byte buffer!,” he added.
References
- ^
James Quinn
(www.binarydefense.com) - ^
new featur
(thehackernews.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/lpFbePN3rI0/emotet-botnet-malware.html