The inner workings of a cybercriminal group known as the Wizard
Spider have been exposed, shedding light on its organizational
structure and motivations.
“Most of Wizard Spider’s efforts go into hacking European and
U.S. businesses, with a special cracking tool used by some of their
attackers to breach high-value targets,” Swiss cybersecurity
company PRODAFT said[1]
in a new report shared with The Hacker News. “Some of the money
they get is put back into the project to develop new tools and
talent.”
Wizard Spider, also known as Gold Blackburn, is believed to
operate out of Russia and refers to a financially motivated threat
actor that’s been linked to the TrickBot botnet, a modular malware
that was officially discontinued[2]
earlier this year in favor of improved malware such as
BazarBackdoor.
That’s not all. The TrickBot operators have also extensively
cooperated with Conti[3], another Russia-linked
cybercrime group notorious for offering ransomware-as-a-service
packages to its affiliates.
Gold Ulrick[4]
(aka Grim Spider), as the group responsible for the distribution of
the Conti (previously Ryuk) ransomware is called, has historically
leveraged initial access provided by TrickBot to deploy the
ransomware against targeted networks.
“Gold Ulrick is comprised of some or all of the same operators
as Gold Blackburn, the threat group responsible for the
distribution of malware such as TrickBot, BazarLoader and Beur
Loader,” cybersecurity firm Secureworks notes[5]
in a profile of the cybercriminal syndicate.
Stating that the group is “capable of monetizing multiple
aspects of its operations,” PRODAFT emphasized the adversary’s
ability to expand its criminal enterprise, which it said is made
possible by the gang’s “extraordinary profitability.”
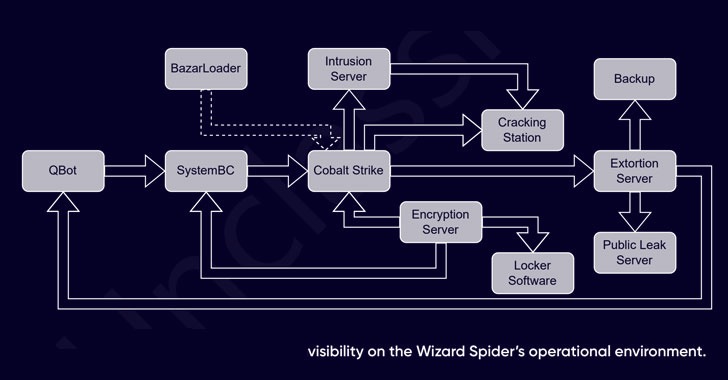
Typical attack chains involving the group commence with spam
campaigns that distribute malware such as Qakbot[6]
(aka QBot) and SystemBC[7], using them as
launchpads to drop additional tools, including Cobalt Strike for
lateral movement, before executing the locker software.
In addition to leveraging a wealth of utilities for credential
theft and reconnaissance, Wizard Spider is known to use an
exploitation toolkit that makes use of recently disclosed
vulnerabilities such as Log4Shell[8]
to gain an initial foothold into victim networks.
Also, put to users a cracking station that hosts cracked hashes
associated with domain credentials, Kerberos tickets, and KeePass
files, among others.
What’s more, the group has invested in a custom VoIP setup
wherein hired telephone operators cold-call non-responsive victims
in a bid to put additional pressure and compel them into paying up
after a ransomware attack.
This is not the first time the group has resorted to such a
tactic. Last year, Microsoft detailed a BazarLoader campaign dubbed
BazaCall[9]
that employed phony call centers to lure unsuspecting victims into
installing ransomware on their systems.
“The group has huge numbers of compromised devices at its
command and employs a highly distributed professional workflow to
maintain security and a high operational tempo,” the researchers
said.
“It is responsible for an enormous quantity of spam on hundreds
of millions of millions of devices, as well as concentrated data
breaches and ransomware attacks on high-value targets.”
References
Read more https://thehackernews.com/2022/05/researchers-expose-inner-working-of.html