Cybersecurity researchers have exposed new connections between a
widely used pay-per-install (PPI) malware service known as
PrivateLoader and another PPI service dubbed ruzki.
“The threat actor ruzki (aka les0k, zhigalsz) advertises their
PPI service on underground Russian-speaking forums and their
Telegram channels under the name ruzki or zhigalsz since at least
May 2021,” SEKOIA[1]
said.
The cybersecurity firm said its investigations into the twin
services led it to conclude that PrivateLoader is the proprietary
loader of the ruzki PPI malware service.
PrivateLoader, as the name implies, functions as a C++-based
loader to download and deploy additional malicious payloads on
infected Windows hosts. It’s primarily distributed through
SEO-optimized websites that claim to provide cracked software.
Although it was first documented[2]
earlier this February by Intel471, it’s said to have been put to
use starting as early as May 2021.
Some of the most common commodity malware families propagated
through PrivateLoader include Redline Stealer, Socelars[3], Raccoon Stealer, Vidar,
Tofsee[4], Amadey, DanaBot, and
ransomware strains Djvu and STOP.
A May 2022 analysis from Trend Micro uncovered the malware
distributing a framework called NetDooka[5]. A follow-up report from
BitSight late last month found[6]
significant infections in India and Brazil as of July 2022.
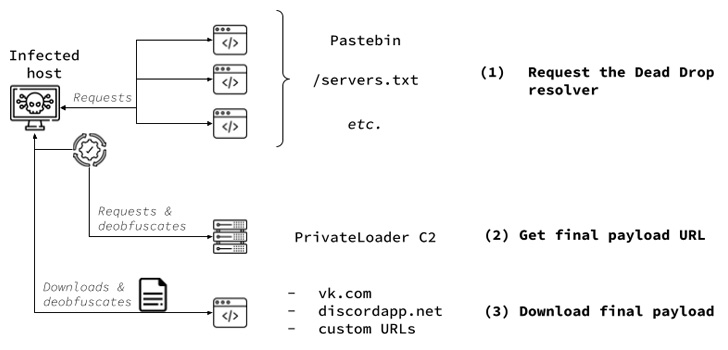
A new change spotted by SEKOIA is the use of VK.com documents
service to host the malicious payloads as opposed to Discord, a
shift likely motivated by increased monitoring[7]
of the platform’s content delivery network.
PrivateLoader is also configured to communicate with
command-and-control (C2) servers to fetch and exfiltrate data. As
of mid-September, there are four active C2 servers, two in Russia
and one each in Czechia and Germany.
“Based on the wide selection of malware families, which implies
a wide range of threat actors or intrusion sets operating this
malware, the PPI service running PrivateLoader is very attractive
and popular to attackers on underground markets,” the researchers
said.
SEKOIA further said it unearthed ties between PrivateLoader and
ruzki, a threat actor that sells bundles of 1,000 installations on
infected systems located across the world ($70), or specifically
Europe ($300) or the U.S. ($1,000).
These advertisements, which have been placed in the Lolz Guru
cybercrime forum, target threat actors (aka prospective customers)
who wish to distribute their payloads through the PPI service.
The association stems mainly from the below observations –
- An overlap between the PrivateLoader C2 servers and that of
URLs provided by ruzki to the subscribers so as to monitor
installation statistics related to their campaigns - References to ruzki in PrivateLoader botnet sample names that
were used to deliver the Redline Stealer, such as ruzki9 and
3108_RUZKI, and - The fact that both PrivateLoader and ruzki commenced operations
in May 2021, with the ruzki operator using the term “our loader” in
Russian on its Telegram channel
“Pay-per-Install services always played a key role in the
distribution of commodity malware,” the researchers said.
“As yet another turnkey solution lowering the cost of entry into
the cybercriminal market and a service contributing to a continuous
professionalization of the cybercriminal ecosystem, it is highly
likely more PrivacyLoader-related activity will be observed in the
short term.”
References
Read more https://thehackernews.com/2022/09/researchers-find-link-bw-privateloader.html