At least three alleged hacktivist groups working in support of
Russian interests are likely doing so in collaboration with
state-sponsored cyber threat actors, according to Mandiant.
The Google-owned threat intelligence and incident response firm
said[1]
with moderate confidence that “moderators of the purported
hacktivist Telegram channels ‘XakNet Team,’ ‘Infoccentr,’ and
‘CyberArmyofRussia_Reborn’ are coordinating their operations with
Russian Main Intelligence Directorate (GRU)-sponsored cyber threat
actors.”
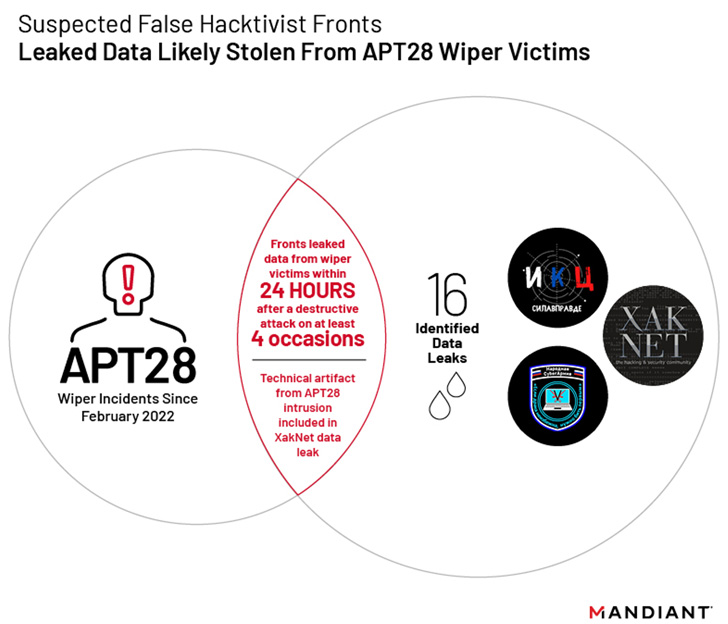
Mandiant’s assessment is based on evidence that the leakage of
data stolen from Ukrainian organizations occurred within 24 hours
of malicious wiper incidents[2] undertaken by the
Russian nation-state group tracked as APT28[3]
(aka Fancy Bear, Sofacy, or Strontium).
To that end, four of the 16 data leaks from these groups
coincided with disk wiping malware attacks[4] by APT28 that involved
the use of a strain dubbed CaddyWiper[5].
APT28[6], active since at least
2009, is associated[7]
with the Russian military intelligence agency, the General Staff
Main Intelligence Directorate (GRU), and drew public attention in
2016 for the breaches of the Democratic National Committee (DNC) in
the run-up to the U.S. presidential election.
While the so-called hacktivist groups have conducted distributed
denial-of-service (DDoS) attacks and website defacements to target
Ukraine, indications are that these fake personas are a front for
information operations and destructive cyber activities.
That said, the exact nature of the relationship and the degree
of affiliation with the Russian state remains unknown, although it
suggests either direct involvement from GRU officers themselves or
through the moderators running the Telegram channels.
This line of reasoning is substantiated by XakNet’s leak of a
“unique” technical artifact that APT28 utilized in its compromise
of a Ukrainian network and the fact that CyberArmyofRussia_Reborn’s
data releases are preceded by APT28 intrusion operations.
The cybersecurity company noted it also unearthed some level of
coordination between the XakNet Team and Infoccentr as well as the
pro-Russia group KillNet[8].
“The war in Ukraine has also presented novel opportunities to
understand the totality, coordination, and effectiveness of Russia
cyber programs, including the use of social media platforms by
threat actors,” Mandiant said.
References
- ^
said
(www.mandiant.com) - ^
malicious wiper incidents
(thehackernews.com) - ^
APT28
(thehackernews.com) - ^
disk
wiping malware attacks (www.fortinet.com) - ^
CaddyWiper
(thehackernews.com) - ^
APT28
(thehackernews.com) - ^
associated
(symantec-enterprise-blogs.security.com) - ^
KillNet
(thehackernews.com)
Read more https://thehackernews.com/2022/09/researchers-identify-3-hacktivist.html