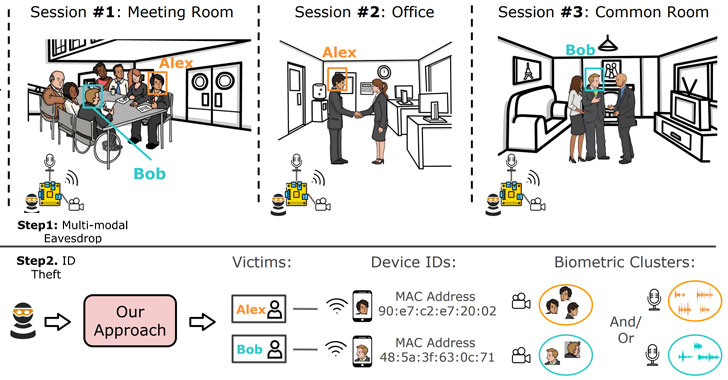
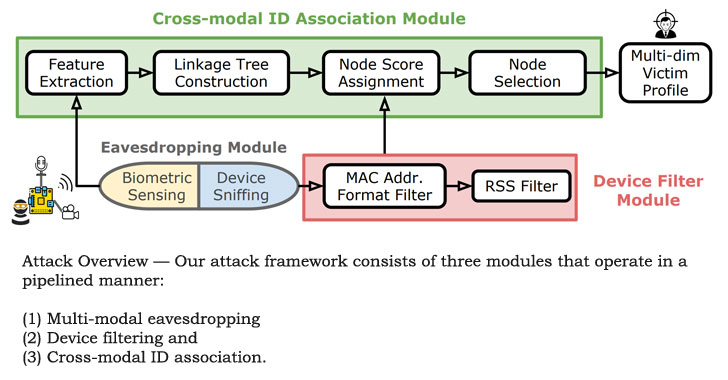
track online users using a novel approach that combines device
identifiers with their biometric information.
The details come from a newly published research[1]
titled “Nowhere to Hide: Cross-modal Identity Leakage between
Biometrics and Devices” by a group of academics from the University
of Liverpool, New York University, The Chinese University of Hong
Kong, and University at Buffalo SUNY.
“Prior studies on identity theft only consider the attack goal
for a single type of identity, either for device IDs or
biometrics,” Chris Xiaoxuan Lu, Assistant Professor at the
University of Liverpool, told The Hacker News in an email
interview. “The missing part, however, is to explore the
feasibility of compromising the two types of identities
simultaneously and deeply understand their correlation in
multi-modal IoT environments.”
The researchers presented the findings at the Web Conference 2020
held in Taipei last week. The prototype and the associated code can
be accessed here.
A Compound Data Leakage Attack
The identity leakage mechanism builds on the idea of surreptitious
eavesdropping of individuals in cyber-physical spaces over extended
periods of time.
uniqueness of individuals’ biometric information (faces, voices,
etc.) and Wi-Fi MAC addresses of smartphones and IoT
devices to automatically identify people by drawing a
spatial-temporal correlation between the two sets of observations.
“The attacker can be either insider like co-workers who share
the same office with victims or outsiders who use their laptops to
eavesdrop random victims in a coffee shop,” Xiaoxuan Lu said. “So
launching such an attack is not difficult, considering multi-modal
IoT devices are very small and can be disguised well, like a spy
camera with Wi-Fi sniffing function. All in all, there is little
setup effort on the side of the attacker.”
To mount the attack, the researchers assembled an eavesdropping
prototype built on a Raspberry Pi that consisted of an audio
recorder, an 8MP camera, and a Wi-Fi sniffer that can capture the
device identifiers.
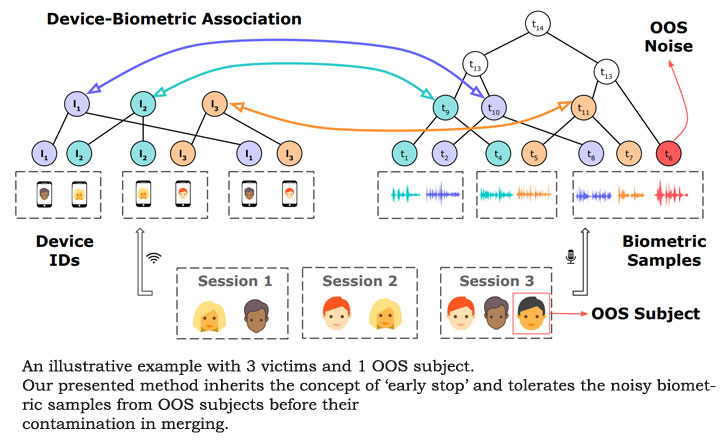
The data collected in this manner not only ascertained that
there exists a session attendance similarity between one’s physical
biometrics and his/her personal device, but they are also unique
enough to isolate a specific individual among several people
located in the same space.
a victim is hidden in a crowd and shares the same or highly similar
session attendance pattern with another subject in the — something
that’s difficult to happen and impractical, according to the
researchers.
Possible Mitigation Techniques
But with billions of IoT devices connected to the internet, the
researchers say the compound effect of such a data leakage is a
real threat, with the adversary capable of deanonymizing over 70%
of the device identifiers.
Obfuscating wireless communications and scanning for hidden
microphones or cameras could help to mitigate the cross-modal
attack, although they warn there is no good countermeasure yet.
“Avoid connecting Wi-Fi to public wireless networks as it leaves
your underlying Wi-Fi MAC address exposed,” Xiaoxuan Lu said.
“Don’t allow multi-modal IoT devices (such as smart doorbell or
voice assistants) to monitor you 24/7, because they send data back
to third parties with no transparency to you, and they can be
easily hacked and can compromise your ID in multiple
dimensions.”
References
- ^
published research
(arxiv.org) - ^
here
(github.com) - ^
MAC addresses
(en.wikipedia.org)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/Qs7wa1w0WkE/deanonymize-device-biometrics.html