The U.S. Cybersecurity and Infrastructure Security Agency (CISA)
on Thursday added[1]
two flaws to its Known Exploited Vulnerabilities
Catalog[2], citing evidence of
active exploitation.
The two high-severity issues relate to weaknesses in Zimbra
Collaboration, both of which could be chained to achieve
unauthenticated remote code execution on affected email servers
–
- CVE-2022-27925[3] (CVSS score: 7.2) –
Remote code execution (RCE) through mboximport from authenticated
user (fixed in versions[4]
8.8.15 Patch 31 and 9.0.0 Patch 24 released in March) - CVE-2022-37042[5] – Authentication bypass
in MailboxImportServlet (fixed in versions[6]
8.8.15 Patch 33 and 9.0.0 Patch 26 released in August)
“If you are running a Zimbra version that is older than Zimbra
8.8.15 patch 33 or Zimbra 9.0.0 patch 26 you should update to the
latest patch as soon as possible,” Zimbra warned[7]
earlier this week.
CISA has not shared any information on the attacks exploiting
the flaws but cybersecurity firm Volexity described[8]
mass in-the-wild exploitation of Zimbra instances by an unknown
threat actor.
In a nutshell, the attacks involve taking advantage of the
aforementioned authentication bypass flaw to gain remote code
execution on the underlying server by uploading arbitrary
files.
Volexity said “it was possible to bypass authentication when
accessing the same endpoint (mboximport) used by CVE-2022-27925,”
and that the flaw “could be exploited without valid administrative
credentials, thus making the vulnerability significantly more
critical in severity.”
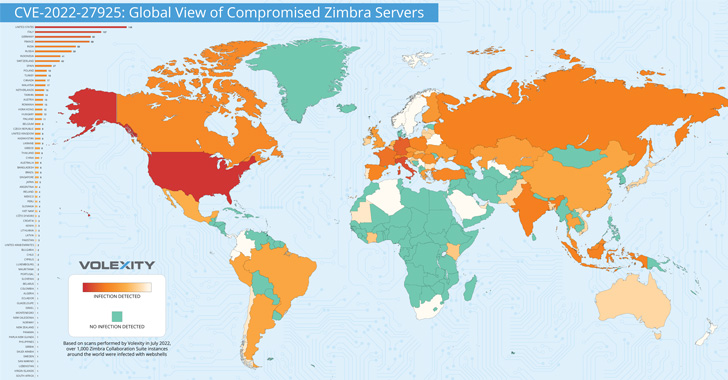
It also singled out over 1,000 instances globally that were
backdoored and compromised using this attack vector, some of which
belong to government departments and ministries; military branches;
and companies with billions of dollars of revenue.
The attacks, which transpired as recently as the end of June
2022, also involved the deployment of web shells to maintain
long-term access to the infected servers. Top countries with the
most compromised instances include the U.S., Italy, Germany,
France, India, Russia, Indonesia, Switzerland, Spain, and
Poland.
“CVE-2022-27925 was originally listed as an RCE exploit
requiring authentication,” Volexity said. “When combined with a
separate bug, however, it became an unauthenticated RCE exploit
that made remote exploitation trivial.”
The disclosure comes a week after CISA added another
Zimbra-related bug, CVE-2022-27924[9], to the catalog, which,
if exploited, could allow attackers to steal cleartext credentials
from users of the targeted instances.
References
- ^
added
(www.cisa.gov) - ^
Known
Exploited Vulnerabilities Catalog
(www.cisa.gov) - ^
CVE-2022-27925
(nvd.nist.gov) - ^
versions
(wiki.zimbra.com) - ^
CVE-2022-37042
(nvd.nist.gov) - ^
versions
(wiki.zimbra.com) - ^
warned
(blog.zimbra.com) - ^
described
(www.volexity.com) - ^
CVE-2022-27924
(thehackernews.com)
Read more https://thehackernews.com/2022/08/researchers-warn-of-ongoing-mass.html