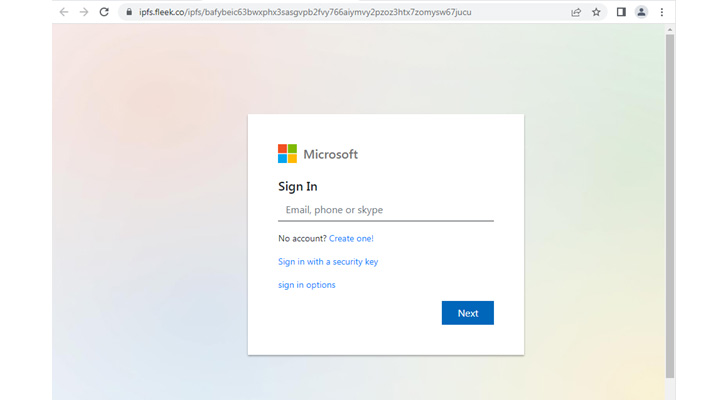
The decentralized file system solution known as IPFS is becoming
the new “hotbed” for hosting phishing sites, researchers have
warned.
Cybersecurity firm Trustwave SpiderLabs, which disclosed
specifics of the attack campaigns, said it identified no less than
3,000 emails containing IPFS phishing URLs as an attack vector in
the last three months.
IPFS[1], short for
InterPlanetary File System, is a peer-to-peer (P2P) network to
store and share files and data using cryptographic hashes, instead
of URLs or filenames, as is observed in a traditional client-server
approach. Each hash forms the basis for a unique content identifier
(CID[2]).
The idea is to create a resilient distributed file system that
allows data to be stored across multiple computers. This would
allow information to be accessed without having to rely on third
parties such as cloud storage providers, effectively making it
resistant to censorship.
“Taking down phishing content stored on IPFS can be difficult
because even if it is removed in one node, it may still be
available on other nodes,” Trustwave researchers Karla Agregado and
Katrina Udquin said[3]
in a report.
Complicating matters further is the lack of a static Uniform
Resource Identifier (URI) that can be used to locate and block a
single piece of malware-laden content. This also means it could be
much harder to take down phishing sites hosted on IPFS.
The attacks observed by Trust typically involve some type of
social engineering to lower the guard of targets in order to coax
them to click fraudulent IPFS links and activate the infection
chains.
These domains prompt potential victims to enter their
credentials to view a document, track a package on DHL, or renew
their Azure subscription, only to siphon the email addresses and
passwords to a remote server.
“With data persistence, robust network, and little regulation,
IPFS is perhaps an ideal platform for attackers to host and share
malicious content,” the researcher said.
The findings come amid a larger shift in the email threat
landscape, with Microsoft’s plans to block macros causing threat
actors to adapt their tactics[4]
to distribute executables that can lead to follow-on
reconnaissance, data theft, and ransomware.
Viewed in that light, the use of IPFS marks another evolution in
phishing, giving attackers another lucrative playground to
experiment with.
“Phishing techniques have taken a leap by utilizing the concept
of decentralized cloud services using IPFS,” the researchers
concluded.
“The spammers can easily camouflage their activities by hosting
their content in legitimate web hosting services or use multiple
URL redirection techniques to help thwart scanners using URL
reputation or automated URL analysis.”
What’s more, these changes have also been accompanied by the use
of off-the-shelf phishing kits – a trend called
phishing-as-a-service (PhaaS[5]) – that offer a quick
and easy means for threat actors to mount attacks via email and
SMS.
Indeed, researchers from IronNet took the wraps off a
large-scale campaign utilizing a four-month-old PhaaS platform
dubbed Robin Banks to plunder credentials and steal financial
information from customers of well-known banks in Australia,
Canada, the U.K., and the U.S.
“While the primary motivation for scammers using this kit
appears to be financial, the kit does also ask victims for their
Google and Microsoft credentials after they travel to the phishing
landing page, indicating it could also be used by more advanced
threat actors looking to gain initial access to corporate networks
for ransomware or other post-intrusion activities,” the researchers
said[6].
References
Read more https://thehackernews.com/2022/07/researchers-warns-of-increase-in.html