Russian state-sponsored actors are continuing to strike
Ukrainian entities with information-stealing malware as part of
what’s suspected to be an espionage operation.
Symantec, a division of Broadcom Software, attributed[1]
the malicious campaign to a threat actor tracked Shuckworm[2], also known as Actinium[3], Armageddon[4], Gamaredon, Primitive
Bear, and Trident Ursa. The findings have been corroborated[5]
by the Computer Emergency Response Team of Ukraine (CERT-UA).
The threat actor, active since at least 2013, is known for
explicitly singling out public and private entities in Ukraine. The
attacks have since ratcheted up in the wake of Russia’s military
invasion in late 2022.
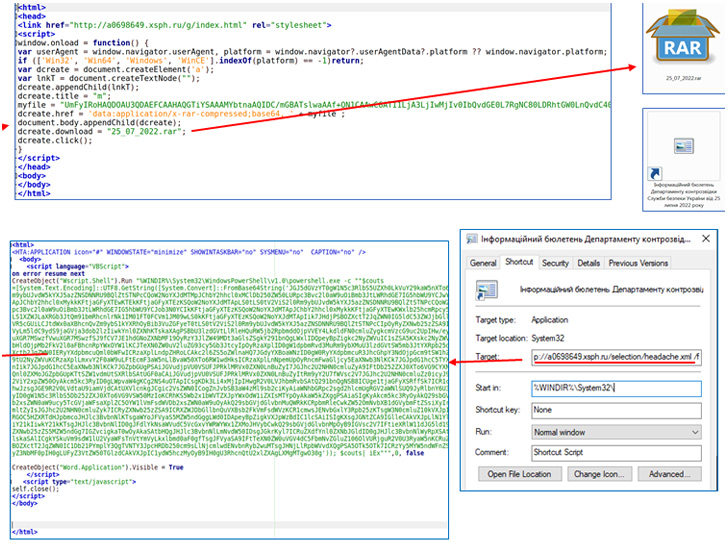
The latest set of attacks are said to have commenced on July 15,
2022, and ongoing as recently as August 8, with the infection
chains leveraging phishing emails disguised as newsletters and
combat orders, ultimately leading to the deployment of a PowerShell
stealer malware dubbed GammaLoad.PS1_v2[6].
Also delivered to the compromised machines are two backdoors
named Giddome and Pterodo, both of which are trademark Shuckworm
tools that have been continually redeveloped by the attackers in a
bid to stay ahead of detection.
At its core, Pterodo[7]
is a Visual Basic Script (VBS) dropper malware[8]
with capabilities to execute PowerShell scripts, use scheduled
tasks (shtasks.exe) to maintain persistence, and download
additional code from a command-and-control server.
The Giddome implant, on the other hand, features several
capabilities, including recording audio, capturing screenshots,
logging keystrokes, and retrieving and executing arbitrary
executables onto the infected hosts.
The intrusions, which occur through emails distributed from
compromised accounts, further leverage legitimate software like
Ammyy Admin and AnyDesk to facilitate remote access.
The findings come as the Gamaredon actor has been linked to a
series of social engineering
attacks[9] aimed at initiating the
GammaLoad.PS1 delivery chain, enabling the threat actor to steal
files and credentials stored in web browsers.
“As the Russian invasion of Ukraine approaches the six-month
mark, Shuckworm’s long-time focus on the country appears to be
continuing unabated,” Symantec noted.
“While Shuckworm is not necessarily the most tactically
sophisticated espionage group, it compensates for this in its focus
and persistence in relentlessly targeting Ukrainian
organizations.”
The findings follow an alert from CERT-UA, which cautioned[10] of “systematic, massive
and geographically dispersed” phishing attacks involving the use of
a .NET downloader called RelicRace to execute payloads such as
Formbook[11] and Snake Keylogger[12].
References
- ^
attributed
(symantec-enterprise-blogs.security.com) - ^
Shuckworm
(thehackernews.com) - ^
Actinium
(thehackernews.com) - ^
Armageddon
(thehackernews.com) - ^
corroborated
(cert.gov.ua) - ^
GammaLoad.PS1_v2
(thehackernews.com) - ^
Pterodo
(symantec-enterprise-blogs.security.com) - ^
dropper
malware (thehackernews.com) - ^
series
of social engineering attacks (cert.gov.ua) - ^
cautioned
(cert.gov.ua) - ^
Formbook
(thehackernews.com) - ^
Snake
Keylogger (thehackernews.com)
Read more https://thehackernews.com/2022/08/russian-state-hackers-continue-to.html