vulnerability affecting the Server Message Block (SMB) protocol
that could allow attackers to leak kernel memory remotely, and when
combined with a previously disclosed “wormable” bug, the flaw can
be exploited to achieve remote code execution attacks.
Dubbed “SMBleed” (CVE-2020-1206[1]) by cybersecurity firm
ZecOps, the flaw resides in SMB’s decompression function — the same
function as with SMBGhost[2] or EternalDarkness bug
(CVE-2020-0796[3]), which came to light
three months ago, potentially opening vulnerable Windows systems to
malware attacks that can propagate across networks.
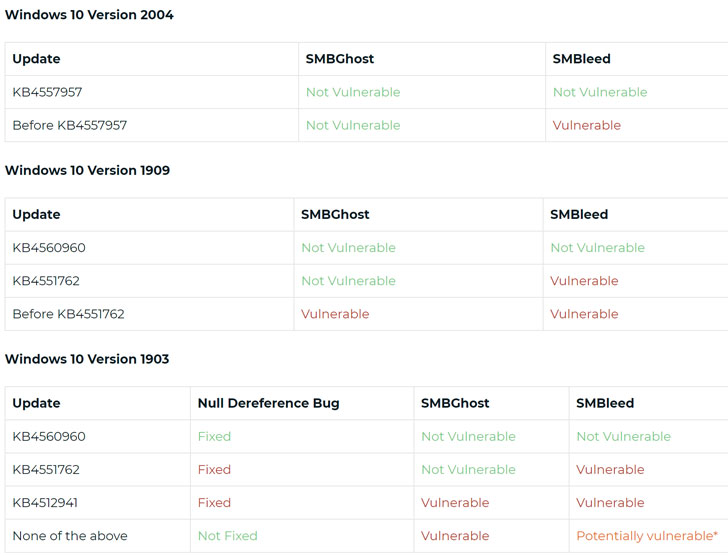
The newly discovered vulnerability impacts Windows 10 versions
1903 and 1909, for which Microsoft today released security patches
as part of its monthly Patch Tuesday
updates for June.
[4]
The development comes as the US Cybersecurity and Infrastructure
Security Agency (CISA) issued an advisory last week warning Windows
10 users to update their machines after exploit code for SMBGhost
bug was published online last week.
SMBGhost was deemed so serious that it received a maximum
severity rating score of 10.
vulnerability in March 2020, malicious cyber actors are
targeting unpatched systems with the new PoC, according to recent open-source
reports,” CISA said.
SMB, which runs over TCP port 445, is a network protocol that
provides the basis for file sharing, network browsing, printing
services, and interprocess communication over a network.
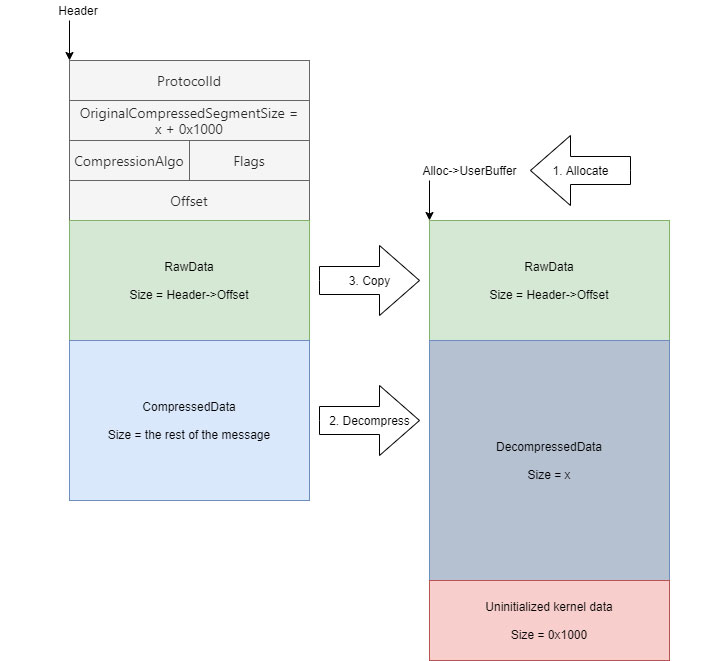
According to ZecOps researchers, the flaw stems from the way the
decompression function in question (“Srv2DecompressData“) handles specially
crafted message requests (e.g., SMB2 WRITE)
sent to a targeted SMBv3 Server, allowing an attacker to read
uninitialized kernel memory and make modifications to the
compression function.
[8][9]
“The message structure contains fields such as the amount of bytes
to write and flags, followed by a variable-length buffer,” the
researchers said. “That’s perfect for exploiting the bug since we
can craft a message such that we specify the header, but the
variable-length buffer contains uninitialized data.”
“An attacker who successfully exploited the vulnerability could
obtain information to further compromise the user’s system. To
exploit the vulnerability against a server, an unauthenticated
attacker could send a specially crafted packet to a targeted SMBv3
server,” Microsoft said in its advisory.
“To exploit the vulnerability against a client, an
unauthenticated attacker would need to configure a malicious SMBv3
server and convince a user to connect to it,” Microsoft added.
systems to achieve remote code execution. The firm has also
released a proof-of-concept exploit code
demonstrating the flaws.
business users install the latest Windows updates as soon as
possible.
For systems where the patch is not applicable, it’s advised to
block port 445 to prevent lateral movement and remote
exploitation.
Microsoft’s security guidance addressing SMBleed and SMBGhost in
Windows 10 version 1909 and 1903 and Server Core for the same
versions can be found
here[12] and here[13].
References
- ^
CVE-2020-1206
(blog.zecops.com) - ^
SMBGhost
(thehackernews.com) - ^
CVE-2020-0796
(nvd.nist.gov) - ^
Patch Tuesday updates for June
(thehackernews.com) - ^
updates for this vulnerability
(thehackernews.com) - ^
new
PoC (github.com) - ^
CISA said
(www.us-cert.gov) - ^
Srv2DecompressData
(blog.zecops.com) - ^
SMB2 WRITE
(docs.microsoft.com) - ^
exploit code demonstrating
(github.com) - ^
flaws
(github.com) - ^
found here
(portal.msrc.microsoft.com) - ^
here
(portal.msrc.microsoft.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/F1ME2wIGUFg/SMBleed-smb-vulnerability.html