The SOVA Android banking trojan is continuing to be actively
developed with upgraded capabilities to target no less than 200
mobile applications, including banking apps and crypto exchanges
and wallets, up from 90 apps when it started out.
That’s according to the latest findings from Italian
cybersecurity firm Cleafy, which found newer versions of the
malware sporting functionality to intercept two-factor
authentication (2FA) codes, steal cookies, and expand its targeting
to cover Australia, Brazil, China, India, the Philippines, and the
U.K.
SOVA, meaning Owl in Russian, came to light in September 2021[1]
when it was observed striking financial and shopping apps from the
U.S. and Spain for harvesting credentials through overlay attacks
by taking advantage of Android’s Accessibility services.
In less than a year, the trojan has also acted as a foundation
for another Android malware called MaliBot[2]
that’s designed to target online banking and cryptocurrency wallet
customers in Spain and Italy.
The latest variant of SOVA, dubbed v4 by Cleafy, conceals itself
within fake applications that feature logos of legitimate apps like
Amazon and Google Chrome to deceive users into installing them.
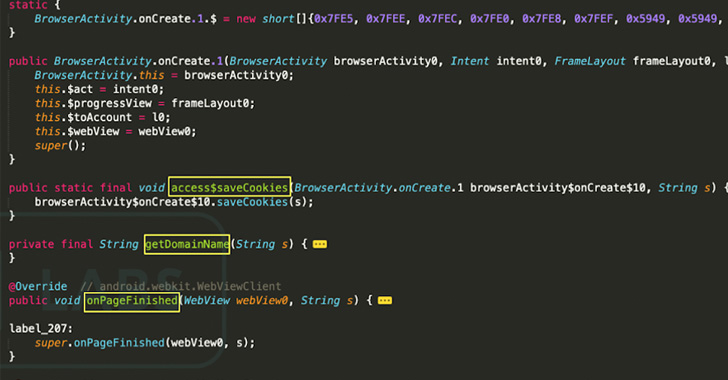
Other notable improvements include capturing screenshots and
recording the device screens.
“These features, combined with Accessibility services, enable
[threat actors] to perform gestures and, consequently, fraudulent
activities from the infected device, as we have already seen in
other Android Banking Trojans (e.g. Oscorp or BRATA),” Cleafy
researchers Francesco Iubatti and Federico Valentini said[3].
SOVA v4 is also notable for its effort to gather sensitive
information from Binance and Trust Wallet, such as account balances
and seed phrases. What’s more, all the 13 Russian and Ukraine-based
banking apps that were targeted by the malware have since been
removed from the version.
To make matters worse, the update enables the malware to
leverage its wide-ranging permissions to deflect uninstallation
attempts by redirecting the victim to the home screen and
displaying the toast message[4]
“This app is secured.”
The banking trojan, feature-rich as it is, is also expected to
incorporate a ransomware component in the next iteration, which is
currently under development and aims to encrypt all files stored in
the infected device using AES[5]
and rename them with the extension “.enc.”
The enhancement is also likely to make SOVA a formidable threat
in the mobile threat landscape.
“The ransomware feature is quite interesting as it’s still not a
common one in the Android banking trojans landscape,” the
researchers said. “It strongly leverages on the opportunity that
has arisen in recent years, as mobile devices became for most
people the central storage for personal and business data.”
References
- ^
September 2021
(thehackernews.com) - ^
MaliBot
(thehackernews.com) - ^
said
(www.cleafy.com) - ^
toast
message (developer.android.com) - ^
AES
(en.wikipedia.org)
Read more https://thehackernews.com/2022/08/sova-android-banking-trojan-returns-new.html