Cybersecurity researchers have offered insight into a previously
undocumented software control panel used by a financially motivated
threat group known as TA505.
“The group frequently changes its malware attack strategies in
response to global cybercrime trends,” Swiss cybersecurity firm
PRODAFT said[1]
in a report shared with The Hacker News. “It opportunistically
adopts new technologies in order to gain leverage over victims
before the wider cybersecurity industry catches on.”
Also tracked under the names Evil Corp, Gold Drake, Dudear,
Indrik Spider, and SectorJ04, TA505 is an aggressive Russian cybercrime syndicate[2] behind the infamous
Dridex banking trojan and which has been linked to a number of ransomware campaigns[3] in recent years.
It’s also said to be connected to the Raspberry Robin attacks[4]
that emerged in September 2021, with similarities uncovered between
the malware and Dridex.
Other notable malware families associated with the group include
FlawedAmmyy[5], Neutrino botnet[6], and a backdoor
codenamed ServHelper[7], one variant of which is
capable of downloading a remote access trojan called FlawedGrace[8].
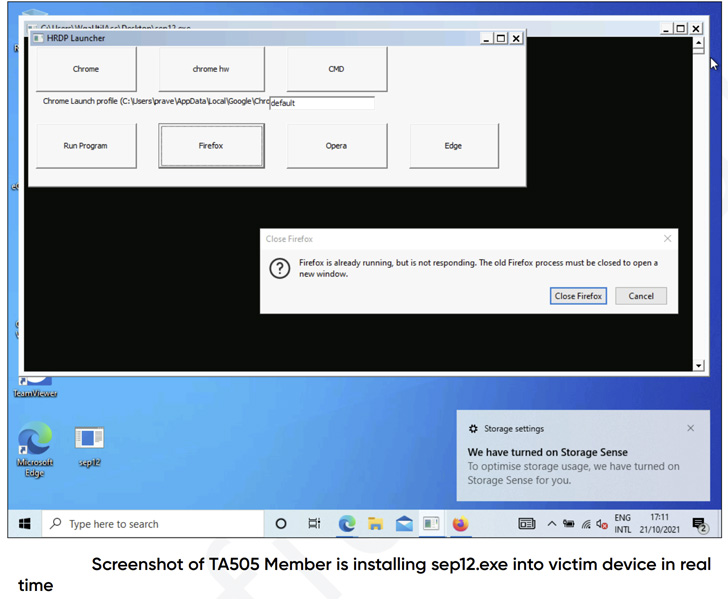
The control panel, called TeslaGun, is said to be used by the
adversary to manage the ServHelper implant, working as a
command-and-control (C2) framework to commandeer the compromised
machines.
Additionally, the panel offers the ability for the attackers to
issue commands, not to mention send a single command to all victim
devices in go or configure the panel such that a predefined command
is automatically run when a new victim is added to the panel.
“The TeslaGun panel has a pragmatic, minimalist design. The main
dashboard only contains infected victim data, a generic comment
section for each victim, and several options for filtering victim
records,” the researchers said.
Aside from using the panel, the threat actors are also known to
employ a remote desktop protocol (RDP) tool to manually connect to
the targeted systems via RDP tunnels[9].
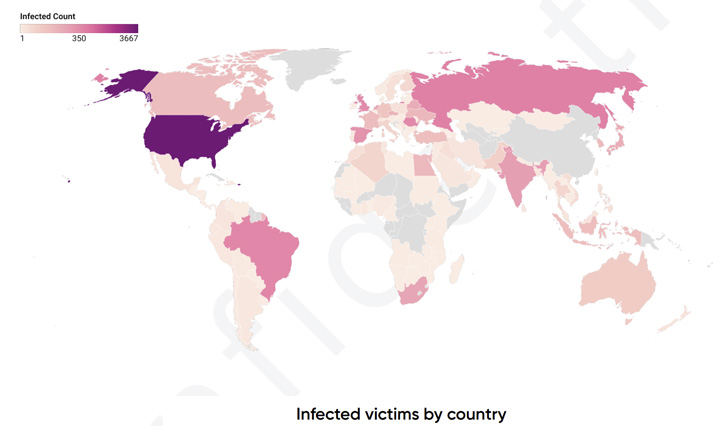
PRODAFT’s analysis of TeslaGun victim data shows that the
group’s phishing and targeted campaigns have hit at least 8,160
targets since July 2020. A majority of those victims are located in
the U.S. (3,667), followed by Russia (647), Brazil (483), Romania
(444), and the U.K. (359).
“It is clear that TA505 is actively looking for online banking
or retail users, including crypto-wallets and e-commerce accounts,”
the researchers noted, citing comments made by the adversarial
group in the TeslaGun panel.
The findings also come as the U.S. Department of Health and
Human Services (HHS) warned of significant threats posed by the
group to the health sector via data exfiltration attacks that aim
to steal intellectual property and ransomware operations.
“Evil Corp has a wide set of highly-capable tools at their
disposal,” the agency’s Health Sector Cybersecurity Coordination
Center (HC3) said[10] in an advisory
published late last month.
“These are developed and maintained in-house, but are often used
in conjunction with commodity malware, living-off-the-land
techniques and common security tools that were designed for
legitimate and lawful security assessments.”
References
- ^
said
(www.prodaft.com) - ^
Russian
cybercrime syndicate (www.truesec.com) - ^
number
of ransomware campaigns (thehackernews.com) - ^
Raspberry Robin attacks
(thehackernews.com) - ^
FlawedAmmyy
(malpedia.caad.fkie.fraunhofer.de) - ^
Neutrino
botnet (www.ptsecurity.com) - ^
ServHelper
(blog.talosintelligence.com) - ^
FlawedGrace
(thehackernews.com) - ^
RDP
tunnels (www.mandiant.com) - ^
said
(www.hhs.gov)
Read more https://thehackernews.com/2022/09/ta505-hackers-using-teslagun-panel-to.html