Five malicious dropper Android apps with over 130,000 cumulative
installations have been discovered on the Google Play Store
distributing banking trojans like SharkBot[1]
and Vultur[2], which are capable of
stealing financial data and performing on-device fraud.
“These droppers continue the unstopping evolution of malicious
apps sneaking to the official store,” Dutch mobile security firm
ThreatFabric told The Hacker News in a statement.
“This evolution includes following newly introduced policies and
masquerading as file managers and overcoming limitations by
side-loading the malicious payload through the web browser.”
Targets of these droppers[3]
include 231 banking and cryptocurrency wallet apps from financial
institutions in Italy, the U.K., Germany, Spain, Poland, Austria,
the U.S., Australia, France, and the Netherlands.
Dropper apps on official app stores like Google Play have
increasingly[4]
become[5]
a popular and efficient technique to distribute banking malware to
unsuspecting users, even as the threat actors behind those
campaigns continually refine their tactics to bypass restrictions[6]
imposed by Google.
The list of malicious apps, four of which are still available on
the digital marketplace, is below –
The latest wave of SharkBot attacks aimed at Italian banking
users since the start of October 2022 entailed the use of a dropper
that masqueraded as an to determine the tax code in the country
(“Codice Fiscale 2022”).
While Google’s Developer Program Policy limits the use of the
REQUEST_INSTALL_PACKAGES
permission[7] to prevent it from being
abused to install arbitrary app packages, the dropper, once
launched, gets around this barrier by opening a fake Google Play
store page impersonating the app listing, leading to the download
of the malware under the guise of an update.
Outsourcing the malware retrieval to the browser is not the only
method adopted by criminal actors. In another instance spotted by
ThreatFabric, the dropper posed as a file manager app, which, per
Google’s revised policy, is a category that’s allowed to have the
REQUEST_INSTALL_PACKAGES permission.
Also spotted were three droppers that offered the advertised
features but also came with a covert function that prompted the
users to install an update upon opening the apps and grant them
permission to install apps from unknown sources, leading to the
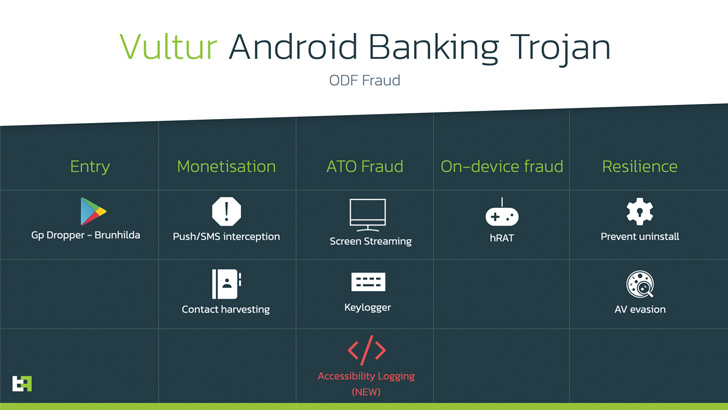
delivery of Vultur.
The new variant of the trojan is notable for adding capabilities
to extensively log user interface elements and interaction events
(e.g., clicks, gestures, etc.), which ThreatFabric said could be a
workaround to the use of the FLAG_SECURE window flag[8]
by banking apps to prevent them from being captured in
screenshots.
The findings from ThreatFabric also come as Cyble uncovered[9]
an upgraded version of the Drinik Android trojan[10] that targets 18 Indian
banks by impersonating the country’s official tax department app to
siphon personal information through the abuse of the accessibility
services API.
“Distribution through droppers on Google Play still remains the
most ‘affordable’ and scalable way of reaching victims for most of
the actors of different levels,” the company noted.
“While sophisticated tactics like telephone-oriented attack
delivery[11] require more resources
and are hard to scale, droppers on official and third-party stores
allow threat actors to reach a wide unsuspecting audience with
reasonable efforts.”
References
- ^
SharkBot
(thehackernews.com) - ^
Vultur
(thehackernews.com) - ^
droppers
(www.threatfabric.com) - ^
increasingly
(thehackernews.com) - ^
become
(thehackernews.com) - ^
bypass
restrictions (support.google.com) - ^
REQUEST_INSTALL_PACKAGES permission
(support.google.com) - ^
FLAG_SECURE window flag
(developer.android.com) - ^
uncovered
(blog.cyble.com) - ^
Drinik
Android trojan (www.cert-in.org.in) - ^
telephone-oriented attack delivery
(thehackernews.com)
Read more https://thehackernews.com/2022/10/these-dropper-apps-on-play-store.html