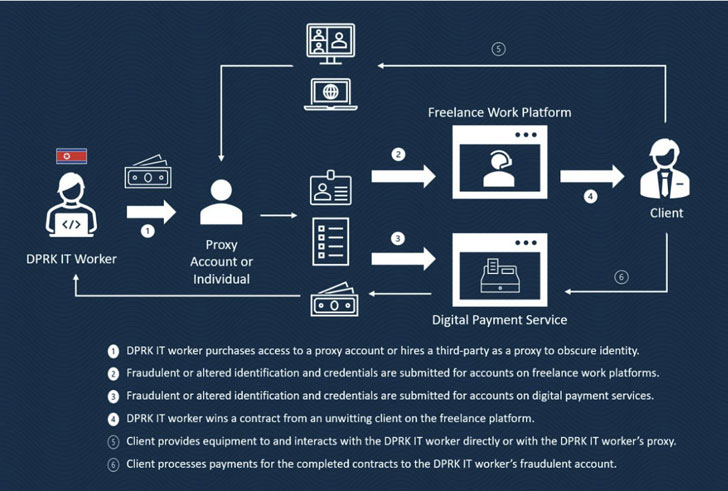
Highly skilled software and mobile app developers from the
Democratic People’s Republic of Korea (DPRK) are posing as
“non-DPRK nationals” in hopes of landing freelance employment in an
attempt to enable the regime’s malicious cyber intrusions[1].
That’s according to a joint advisory[2]
from the U.S. Department of State, the Department of the Treasury,
and the Federal Bureau of Investigation (FBI) issued on Monday.
Targets include financial, health, social media, sports,
entertainment, and lifestyle-focused companies located in North
America, Europe, and East Asia, with most of the dispatched workers
situated in China, Russia, Africa, and Southeast Asia.
The goal, the U.S. agencies warn, is to generate a constant
stream of revenue that sidesteps international sanctions imposed on
the nation and help serve its economic and security priorities,
including the development of nuclear and ballistic missiles.
“The North Korean government withholds up to 90 percent of wages
of overseas workers which generates an annual revenue to the
government of hundreds of millions of dollars,” the guidance
noted.
Some of the core areas where DPRK IT workers have been found to
engage are software development; crypto platforms; graphic
animation; online gambling; mobile games; dating, AI, and VR apps;
hardware and firmware development; biometric recognition software;
and database management.
DPRK IT workers are also known to take on projects that involve
virtual currency, reflecting the country’s continued[3]
interest[4]
in the technology and its history of targeted[5]
attacks[6]
aimed at the financial sector.
Additionally, they are said to abuse the privileged access
obtained as contractors to provide logistical support to North
Korean state-sponsored groups, share access to virtual
infrastructure, facilitate the sale of stolen data, and assist in
money laundering and virtual currency transfers.
Besides deliberately obfuscating their identities, locations,
and nationality online by using VPNs and misrepresenting themselves
as South Korean citizens, potential red flags indicating the
involvement of DPRK IT workers are as follows –
- Multiple logins into one account from various IP addresses in a
short period - Logging into multiple accounts on the same platform from one IP
address - Logged into accounts continuously for one or more days at a
time - Use of ports such as 3389[7]
that are associated with remote desktop sharing software - Using rogue client accounts on freelance work platforms to
boost developer account ratings - Multiple developer accounts receiving high ratings from one
client account in a short time - Frequent money transfers through payment platforms to
China-based bank accounts, and - Seeking payment in virtual currency
In one instance highlighted in the advisory, North Korean
developers working for an unnamed U.S. company carried out an
unauthorized theft of over $50,000 in 30 small installments without
the firm’s knowledge over the course of several months.
“Hiring or supporting the activities of DPRK IT workers poses
many risks, ranging from theft of intellectual property, data, and
funds to reputational harm and legal consequences, including
sanctions under both United States and United Nations authorities,”
the U.S. State Department said.
The advisory also comes as the department announced[8]
a $5 million reward last month for information that leads to the
disruption of North Korea’s cryptocurrency theft, cyber-espionage,
and other illicit nation-state activities.
References
Read more https://thehackernews.com/2022/05/us-warns-against-north-korean-hackers.html