This is great Can you focus on anomaly detecction a bit more in maybe a future article . what are the primary factors ueba/uba systems focus on ? consistent behaviour by user or once in a while deviations or consistent deviation from norm from norm which over time becomes normal 🙂 Will UEBA alogorihtms be able to distinguiush ? many users even in real life tend to deviate in their pattern especially when analysing Internet Browser behaviour like i do . I would think UEBA as a core in threat detection would take note that humans are pretty irrational … maybe a focus on system anomalous behaviour as misbehaviour or anomalous operations by hardware or software events can be more easily detected via SIEM . or thats what the entity in the UEBA acronym means . just thinking out loud . or what really are the differences between UEBA UBA SIEM etc Thanks again for this .
UEBA (User and Entity Behavior Analytics) and UBA (User Behavior Analytics) are closely related concepts in the field of cybersecurity, and the terms are sometimes used interchangeably. However, there is a subtle difference between the two:
User Behavior Analytics (UBA):
User Behavior Analytics focuses primarily on analyzing and monitoring the behavior of individual users within an organization’s network or systems. UBA solutions use machine learning algorithms and advanced analytics to establish a baseline of normal user behavior. Once this baseline is established, the UBA system can detect anomalies or deviations from the norm that may indicate security threats.
UBA typically looks at user activities such as login patterns, file access, application usage, and other interactions with IT systems. When unusual or suspicious behavior is detected, the UBA system can trigger alerts for security teams to investigate further. UBA is often used for insider threat detection, identifying compromised accounts, and improving overall security by pinpointing abnormal user activity.
User and Entity Behavior Analytics (UEBA):
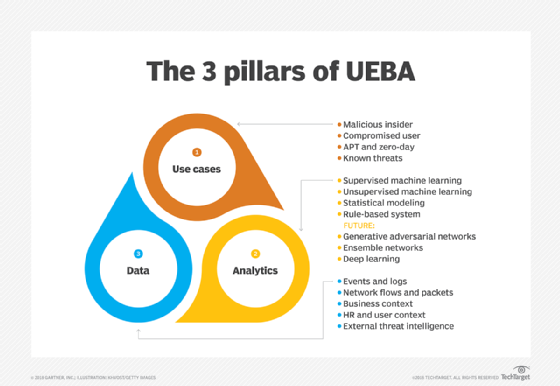
UEBA, on the other hand, expands the scope beyond individual users to include entities, which can be users, devices, applications, or any digital entity within the network. UEBA solutions take into account the behavior of both users and non-user entities and analyze their interactions and relationships.
In addition to monitoring user behavior, UEBA considers entity behavior, including device behavior, application behavior, and the interactions and relationships between these entities. This broader perspective enables UEBA to detect complex and sophisticated threats that may involve multiple entities working together.
UEBA is particularly effective for detecting advanced threats, insider collusion, and attacks involving compromised devices or applications. By analyzing the behavior of entities in context, UEBA provides a more comprehensive view of the security landscape within an organization.
In summary, the key difference is that UBA primarily focuses on individual user behavior analysis, while UEBA extends the analysis to include a broader range of entities, providing a more holistic view of security threats and anomalies. UEBA is often considered a more advanced and comprehensive approach to behavior analytics in cybersecurity.