The threat actor behind a remote access trojan called RomCom RAT
has been observed targeting Ukrainian military institutions as part
of a new spear-phishing campaign that commenced on October 21,
2022.
The development marks a shift in the attacker’s modus operandi,
which has been previously attributed to spoofing legitimate apps
like Advanced IP Scanner and pdfFiller to drop backdoors on
compromised systems.
“The initial ‘Advanced IP Scanner’ campaign occurred on July 23,
2022,” the BlackBerry research and intelligence team said[1]. “Once the victim
installs a Trojanized bundle, it drops RomCom RAT to the
system.”
While previous iterations of the campaign involved the use of
trojanized Advanced IP Scanner, the unidentified adversarial
collective has since switched to pdfFiller as of October 20,
indicating an active attempt on part of the adversary to refine
tactics and thwart detection.
These lookalike websites host a rogue installer package that
results in the deployment of the RomCom RAT, which is capable of
harvesting information and capturing screenshots, all of which is
exported to a remote server.
The adversary’s latest activity directed against the Ukrainian
military is a departure in that it employs a phishing email with an
embedded link as an initial infection vector, leading to a fake
website dropping the next stage downloader.
This downloader, signed using a valid digital certificate[2] from “Blythe Consulting
sp. z o.o.” for an extra layer of evasion, is then used to extract
and run the RomCom RAT malware. BlackBerry said the same signer is
used by the legitimate version of pdfFiller.
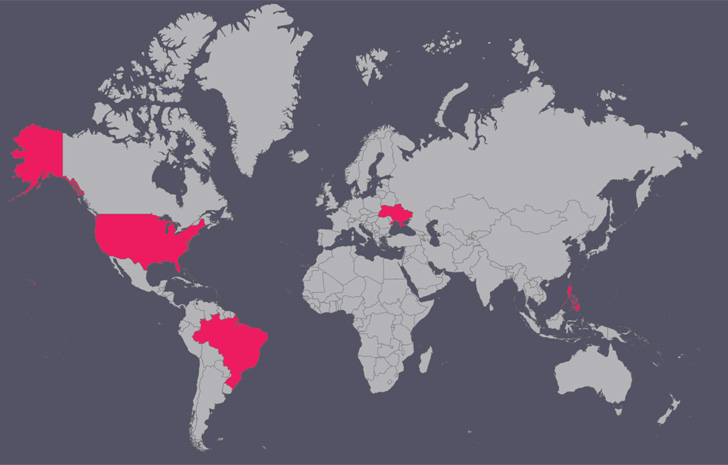
Besides the Ukrainian military, other targets of the campaign
include IT companies, food brokers, and food manufacturing entities
in the U.S., Brazil, and the Philippines.
“This campaign is a good example of the blurred line between
cybercrime-motivated threat actors and targeted attack threat
actors,” Dmitry Bestuzhev, threat researcher at BlackBerry, told
The Hacker News.
“In the past, both groups acted independently, relying on
different tooling. Today, targeted attack threat actors rely more
on traditional tooling, making attribution harder.”
References
- ^
said
(blogs.blackberry.com) - ^
valid
digital certificate (support.microsoft.com)
Read more https://thehackernews.com/2022/10/romcom-hackers-circulating-malicious.html