Virtualization services provider VMware on Tuesday shipped
updates to address 10 security flaws[1] affecting multiple
products that could be abused by unauthenticated attackers to
perform malicious actions.
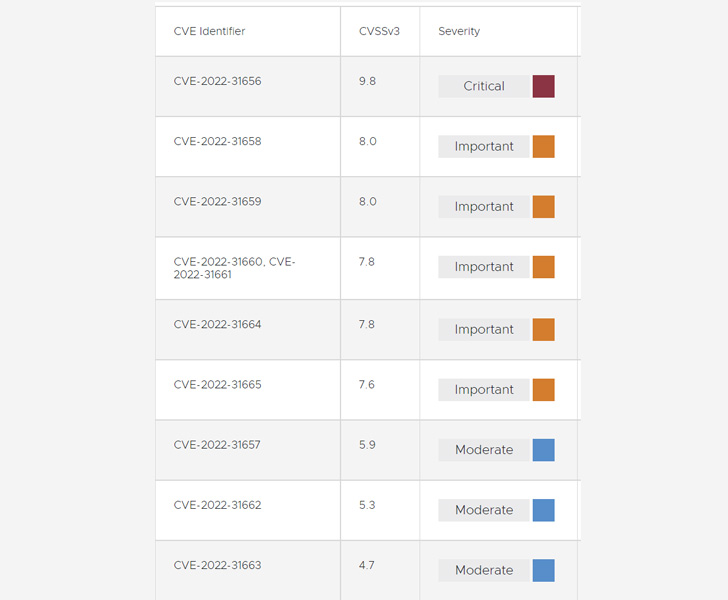
The issues tracked from CVE-2022-31656 through CVE-2022-31665
(CVSS scores: 4.7 – 9.8) affect the VMware Workspace ONE Access,
Workspace ONE Access Connector, Identity Manager, Identity Manager
Connector, vRealize Automation, Cloud Foundation, and vRealize
Suite Lifecycle Manager.
The most severe of the flaws is CVE-2022-31656 (CVSS score:
9.8), an authentication bypass vulnerability affecting local domain
users that could be leveraged by a bad actor with network access to
obtain administrative access.
Also resolved by VMware are three remote code execution
vulnerabilities (CVE-2022-31658, CVE-2022-31659, and
CVE-2022-31665) related to JDBC and SQL injection that could be
weaponized by an adversary with administrator and network
access.
Elsewhere, it has also remediated a reflected cross-site
scripting (XSS) vulnerability (CVE-2022-31663) that it said is a
result of improper user sanitization, which could lead to the
activation of malicious JavaScript code.
Rounding off the patches are three local privilege escalation
bugs (CVE-2022-31660, CVE-2022-31661, and CVE-2022-31664) that
permit an actor with local access to escalate privileges to “root,”
a URL injection vulnerability (CVE-2022-31657), and a path
traversal bug (CVE-2022-31662).
While successful exploitation of CVE-2022-31657 makes it
possible to redirect an authenticated user to an arbitrary domain,
CVE-2022-31662 could equip an attacker to read files in an
unauthorized manner.
VMware said it’s not aware of the exploitation of these
vulnerabilities in the wild, but urged customers using the
vulnerable products to apply the patches immediately[2] to mitigate potential
threats.
References
- ^
address
10 security flaws (www.vmware.com) - ^
apply
the patches immediately (core.vmware.com)
Read more https://thehackernews.com/2022/08/vmware-releases-patches-for-several-new.html