been rolling out a critical software update to its enterprise
customers that patches multiple security vulnerabilities affecting
Citrix ShareFile content collaboration platform.
The security advisory—about which The Hacker News learned from
Dimitri van de
Giessen[1], an ethical hacker and
system engineer—is scheduled to be available publicly later today
on the Citrix
website[2].
Citrix ShareFile is an enterprise-level file sharing solution
for businesses using which employees can securely exchange
proprietary and sensitive business data with each other.
The software offers an on-premises secure cloud environment for
data storage with auditing capabilities and regulatory compliance
controls. For example, a company can remotely lock or wipe data
from potentially compromised mobile devices, or they’re when lost
or stolen.
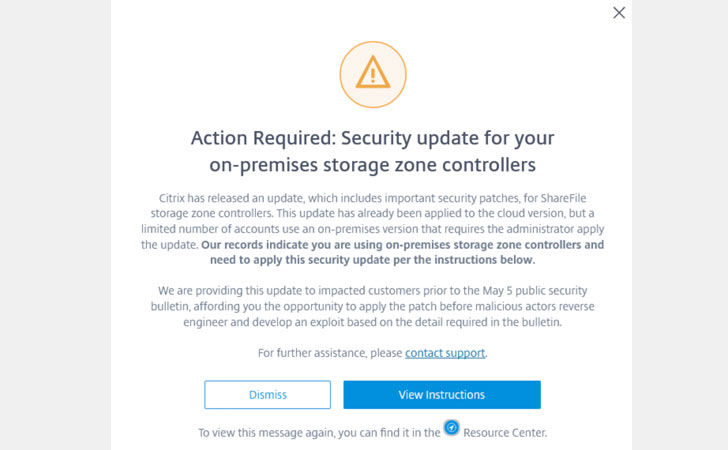
The newly identified security issues (CTX-CVE-2020-7473)
specifically affect customer-managed on-premises Citrix ShareFile
storage zone controllers, a component that stores corporate data
behind the firewall.
The list of vulnerabilities are:
- CVE-2020-7473
- CVE-2020-8982
- CVE-2020-8983
allow an unauthenticated attacker to compromise the storage zones
controller potentially and access sensitive ShareFile documents and
folders.
List of Affected and Patched Citrix ShareFile Versions
If your company uses on-premises ShareFile storage zones controller
versions 5.9.0 / 5.8.0 /5.7.0/ 5.6.0 / 5.5.0 and earlier, you are
affected and recommended to immediately upgrade your platform to
Storage zones controller 5.10.0 / 5.9.1 / 5.8.1 or later.
It is important to note that if your storage zone was created on
any of the affected versions, merely upgrading your software to a
patched version would not completely resolve the
vulnerability.
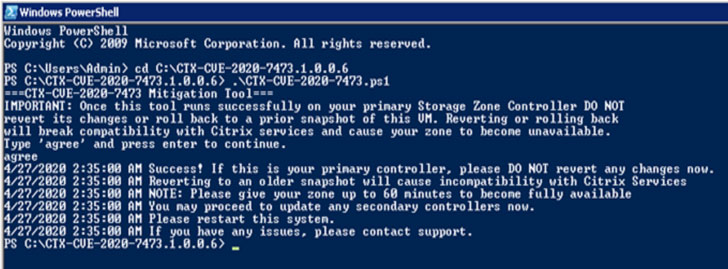
To fix this, the company has separately released a mitigation tool
that you need to be run on your primary Storage zones controller
first and then on any secondary controllers.
“Once the tool runs successfully on your primary zone, you MUST
NOT revert any changes to it. Reverting changes will cause your
zone to become unavailable,” the advisory warned.
You can find a complete step by step details in the advisory, as
soon as it becomes available publicly.
storage zone controllers were also affected, but the company has
already patched them and doesn’t require any further action from
users.
Where the Flaw Resides?
At the time of writing, though not much technical details on the
underlying vulnerabilities are available, an initial patch
inspection by Dimitri reveals that at least one of the flaws could
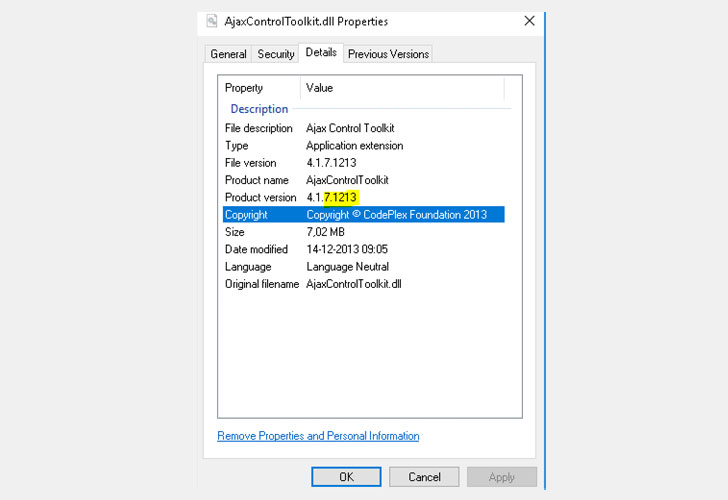
have resided in an old ASP.net Toolkit that Citrix Sharefile used.
The 9-year-old outdated version of AjaxControlToolkit that’s
allegedly bundled with the affected versions of ShareFile software
contains directory traversal and remote code execution
vulnerabilities (CVE-2015-4670[3]), which were disclosed
publicly in 2015.
can visit the following URL in the browser, and if the page returns
blank, it’s vulnerable, and if it through 404 error, it’s either
not flawed or has already been patched.
https://yoursharefileserver.companyname.com/UploadTest.aspx
web.config file and then also deletes UploadTest.aspx and
XmlFeed.aspx from the affected servers.
References
- ^
Dimitri van de Giessen
(twitter.com) - ^
Citrix website
(support.citrix.com) - ^
CVE-2015-4670
(www.cardinaleconcepts.com)
Read more http://feedproxy.google.com/~r/TheHackersNews/~3/HDQcKEZu3TQ/citrix-sharefile-vulnerability.html