Cybersecurity researchers are calling attention to a zero-day
flaw in Microsoft Office that could be abused to achieve arbitrary
code execution on affected Windows systems.
The vulnerability came to light after an independent
cybersecurity research team known as nao_sec uncovered a Word
document (“05-2022-0438.doc[1]“) that was uploaded to
VirusTotal from an IP address in Belarus.
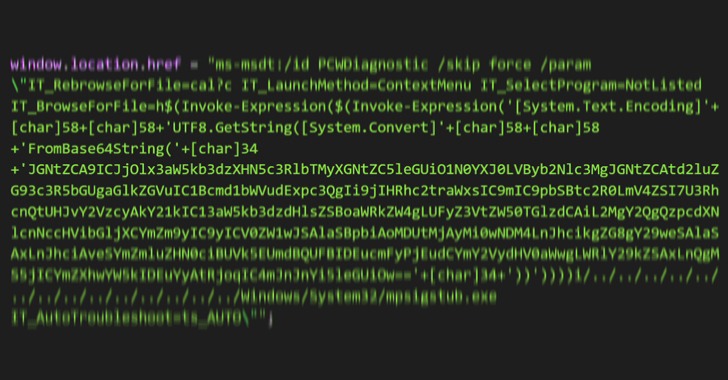
“It uses Word’s external link to load the HTML and then uses the
‘ms-msdt’ scheme to execute PowerShell code,” the researchers
noted[2]
in a series of tweets last week.
According to security researcher Kevin Beaumont, who dubbed the
flaw “Follina,” the maldoc leverages Word’s remote template[3]
feature to fetch an HTML file from a server, which then makes use
of the “ms-msdt://” URI scheme to run the malicious payload.
MSDT[4]
is short for Microsoft Support Diagnostics Tool, a utility that’s
used to troubleshoot and collect diagnostic data for analysis by
support professionals to resolve a problem.
“There’s a lot going on here, but the first problem is Microsoft
Word is executing the code via msdt (a support tool) even if macros
are disabled,” Beaumont explained[5].
“Protected View[6]
does kick in, although if you change the document to RTF form, it
runs without even opening the document (via the preview tab in
Explorer) let alone Protected View,” the researcher added.
Multiple Microsoft Office versions, including Office, Office
2016, and Office 2021, are said to be affected, although other
versions are expected to be vulnerable as well.
What’s more, Richard Warren of NCC Group managed[7]
to demonstrate an exploit on Office Professional Pro with April
2022 running on an up-to-date Windows 11 machine with the preview
pane enabled.
“Microsoft are going to need to patch it across all the
different product offerings, and security vendors will need robust
detection and blocking,” Beaumont said. We have reached out to
Microsoft for comment, and we’ll update the story once we hear
back.
References
- ^
05-2022-0438.doc
(www.virustotal.com) - ^
noted
(twitter.com) - ^
remote
template (attack.mitre.org) - ^
MSDT
(docs.microsoft.com) - ^
explained
(doublepulsar.com) - ^
Protected View
(support.microsoft.com) - ^
managed
(twitter.com)
Read more https://thehackernews.com/2022/05/watch-out-researchers-spot-new.html