-
A user access control policy
- A data classification policy(Correct)
- A perimeter security policy
- An encryption policy
Explanation
AI
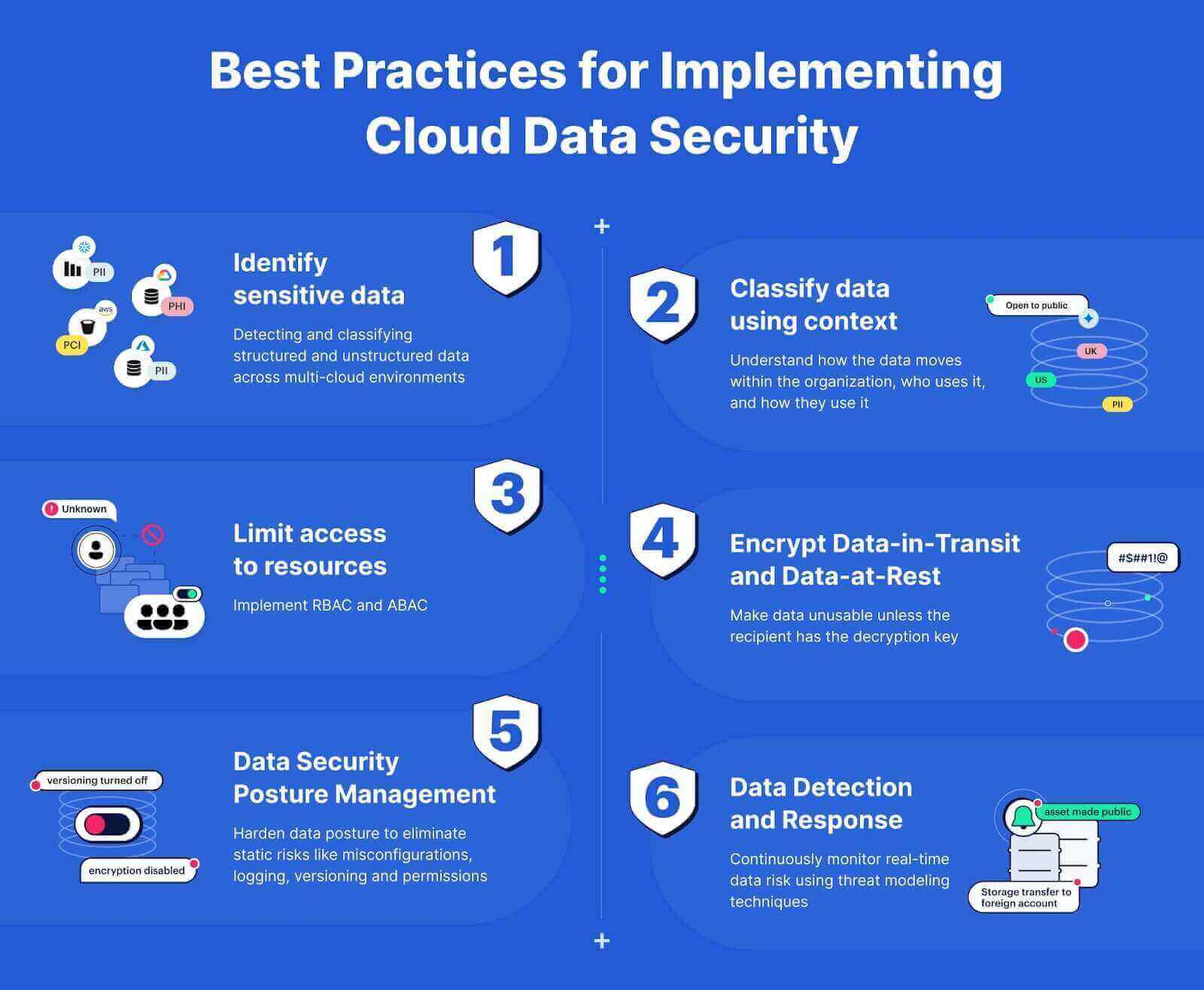
The most effective security policy for protecting sensitive data in a cloud environment is a layered approach that combines multiple security controls to protect data at all stages of its lifecycle, from creation to disposal. This approach should include the following key elements:
Data classification and identification: Identify and classify all sensitive data based on its level of confidentiality, integrity, and availability. This will help to determine the appropriate level of protection required for each type of data.
Access control: Implement strong access controls to restrict access to sensitive data to authorized users only. This includes using strong passwords, multi-factor authentication, and role-based access control (RBAC).
Data encryption: Encrypt sensitive data at rest and in transit to protect it from unauthorized access. This includes encrypting data stored in cloud storage, data transmitted over public networks, and data processed in cloud applications.
Data loss prevention (DLP): Implement DLP solutions to prevent sensitive data from being leaked or exfiltrated from the cloud environment. This includes using DLP tools to monitor data flows, detect unauthorized data transfers, and prevent data from being copied to unauthorized devices.
Vulnerability management: Regularly scan cloud systems and applications for vulnerabilities and patch them promptly. This includes using vulnerability scanning tools and applying security patches from cloud service providers.
Incident response: Have a plan in place to respond to security incidents in a timely and effective manner. This includes identifying the scope of the incident, containing the damage, eradicating the threat, and recovering from the incident.
Security awareness and training: Provide security awareness and training to all cloud users to help them understand the importance of cloud security and how to protect sensitive data. This includes training users on how to create strong passwords, spot phishing attempts, and report security incidents.
Cloud provider security: Choose a reputable cloud service provider (CSP) that has a strong security track record and offers a comprehensive set of security controls. This includes reviewing the CSP’s security policies, procedures, and certifications.
Continuous monitoring: Continuously monitor cloud systems and applications for suspicious activity. This includes using security monitoring tools to detect unauthorized access, anomalous behavior, and potential security threats.
Compliance: Ensure that your cloud environment complies with all applicable laws and regulations. This includes industry-specific regulations such as HIPAA and PCI DSS, as well as data privacy laws such as GDPR and CCPA.
Regular review and update: Regularly review and update your cloud security policy to reflect changes in the cloud environment, threats, and regulations. This includes conducting regular risk assessments and updating security controls accordingly.
By implementing a layered approach to cloud security and following these best practices, organizations can effectively protect their sensitive data in the cloud environment.