Every SaaS app user and login is a potential threat; whether
it’s bad actors or potential disgruntled former associates,
identity management and access control is crucial
to prevent unwanted or mistaken entrances to the organization’s
data and systems.
Since enterprises have thousands to tens of thousands of users,
and hundreds to thousands of different apps, ensuring each entrance
point and user role is secure is no easy feat. Security teams need
to monitor all identities to ensure that user activity meets their
organization’s security guidelines.
Identity and Access Management (IAM) solutions administer user
identities and control access to enterprise resources and
applications. As identities became the new perimeter, making sure
this area is governed by the security team is vital.
Gartner has recently named a new security discipline called
Identity Threat Detection and Response (ITDR) that incorporates
detection mechanisms that investigate suspicious posture changes
and activities, and responds to attacks to restore the integrity of
the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance
methodologies and best practices that are found in SaaS Security
Posture Management solutions (SSPM), enabling security teams to
gain continuous and consolidated visibility of user accounts,
permissions, and privileged activities across the SaaS stack, such
as:
- Identifying who is accessing what and when, and with the right
levels of privileges - Forensics related to user actions, focusing on privileged
users - Roles’ continuous and automated discovery and
consolidation - Role right-sizing by revoking unnecessary or unwanted
access
Whether you are a CISO, IT or on the Governance, Risk and
Compliance (GRC) team, this article will cover the role of Identity
and Access Management Governance as part of the organization’s SaaS
security program.
Learn how to implement IAM governance in
your SaaS Security.[1]
What is IAM Governance
IAM Governance enables the security team to act upon
arising issues by providing constant monitoring of the company’s
SaaS Security posture as well as its implementation of access
control.
There are a few critical prevention domains where an SSPM, like
Adaptive Shield[2], can manage Identity and
Access Management Governance: 1) Misconfigurations 2)
Vulnerabilities 3) Exposure.
Misconfigurations
IAM controls need to be properly configured on a continuous
basis. The IAM configurations should be monitored for any
suspicious changes and ensure that the appropriate steps are taken
to investigate and remediate when relevant.
For example, an organization can enable MFA across the
organization and not require it. This gap in policy enforcement can
leave the organization at risk — and an SSPM can alert the security
team about this gap.
Vulnerabilities
The SSPM solution can utilize patching or compensating controls
to address commonly exploited vulnerabilities in the identity
infrastructure such as the SaaS user’s device. For example, a
privileged CRM user can present a high risk to the company if their
device is vulnerable. To remediate potential threats that stem from
devices, security teams need to be able to correlate SaaS app
users, roles, and permissions with their associated devices’
hygiene. This end-to-end tactic enables a holistic zero-trust
approach to SaaS security.
Another critical vulnerability stems from authentication
protocols that the password access is limited to a single-factor
authentication method, such as with legacy protocols like
IMAP, POP, SMTP and Messaging API (MAPI). An SSPM can identify
where these protocols are in place across the organization’s SaaS
stack.
Exposure
The SSPM helps to reduce the attack surface by identifying and
mitigating places of exposure. For example, removing unnecessary or
excessive privileges or allowing an external admin for a
business-critical app. (See figure 1.)
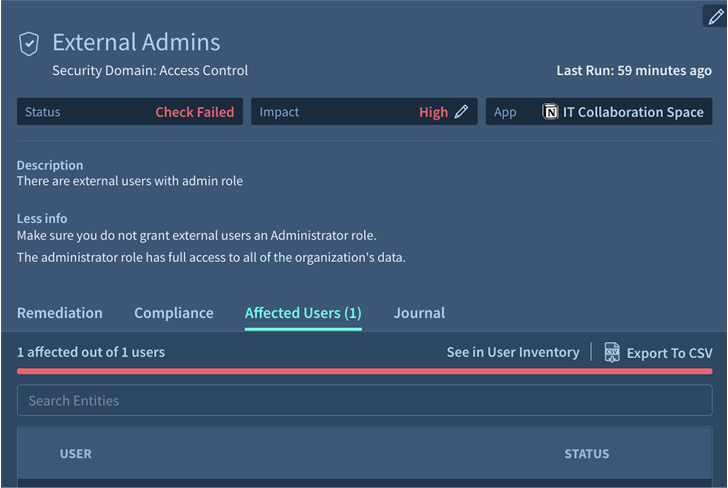 |
| Figure 1. Adaptive Shield’s security check for external admins |
Additionally, 3rd party app access, also known as SaaS-to-SaaS
access can leave an organization exposed. Users connect one app to
another app to either provide enhanced features or user’s
information (e.g contacts, files, calendar, etc). This connection
boosts workflow efficiency and as a result, employees’ workspaces
are connected to multitudes of different apps. However, the
security team is most often in the dark about which apps have been
connected to their organization’s ecosystem, unable to monitor or
mitigate any threats.
Wrap-Up
IAM is a method for hardening access control, whereas IAM
Governance in SSPMs offer continuous monitoring of these features
to ensure security teams have full visibility and control of what’s
happening in the domain.
Get a live demo to learn how to gain
Identity and Access Governance for your SaaS stack.[3]
References
- ^
Learn
how to implement IAM governance in your SaaS Security.
(www.adaptive-shield.com) - ^
Adaptive
Shield (www.adaptive-shield.com) - ^
Get a
live demo to learn how to gain Identity and Access Governance for
your SaaS stack. (www.adaptive-shield.com)
Read more https://thehackernews.com/2022/11/why-identity-access-management.html
