Security flaws have been identified in Xiaomi Redmi Note 9T and
Redmi Note 11 models, which could be exploited to disable the
mobile payment mechanism and even forge transactions via a rogue
Android app installed on the devices.
Check Point said it found the flaws in devices powered by
MediaTek chipsets during a security analysis of the Chinese handset
maker’s “Kinibi” Trusted Execution Environment (TEE).
A TEE refers to a secure enclave[1]
inside the main processor that’s used to process and store
sensitive information such as cryptographic keys so as to ensure
confidentiality and integrity.
Specifically, the Israeli cybersecurity firm discovered that a
trusted app on a Xiaomi device can be downgraded due to a lack of
version control, enabling an attacker to replace a newer, secure
version of an app with an older, vulnerable variant.
“Therefore, an attacker can bypass security fixes made by Xiaomi
or MediaTek in trusted apps by downgrading them to unpatched
versions,” Check Point researcher Slava Makkaveev said[2]
in a report shared with The Hacker News.
Additionally, several vulnerabilities have been identified in
“thhadmin,” a trusted app that’s responsible for security
management, which could be abused by a malicious app to leak stored
keys or to execute arbitrary code in the context of the app.
“We discovered a set of vulnerabilities that could allow forging
of payment packages or disabling the payment system directly from
an unprivileged Android application,” Makkaveev said in a statement
shared with The Hacker News.
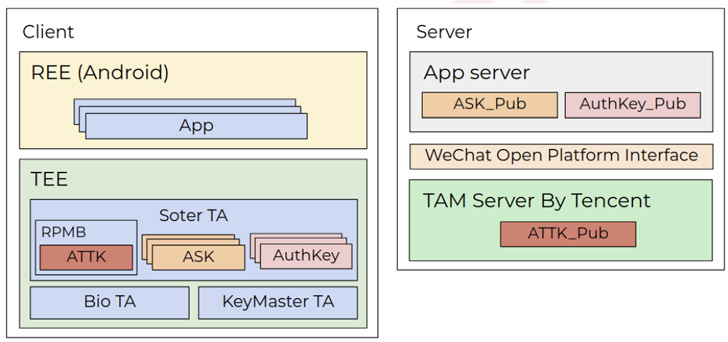
The weaknesses take aim at a trusted app developed by Xiaomi to
implement cryptographic operations related to a service called
Tencent Soter[3], which is a “biometric
standard” that functions as an embedded mobile payment framework to
authorize transactions on third-party apps using WeChat and
Alipay.
But a heap overflow vulnerability in the soter trusted app meant
that it could be exploited to induce a denial-of-service by an
Android app that has no permissions to communicate with the TEE
directly.
That’s not all. By chaining the aforementioned downgrade attack
to replace the soter trusted app to an older version that contained
an arbitrary read vulnerability, Check Point found it was possible
to extract the private keys used to sign payment packages.
“The vulnerability […] completely compromises the Tencent
soter platform, allowing an unauthorized user to sign fake payment
packages,” the company noted.
Xiaomi, following responsible disclosure, has rolled out
patches[4]
to address CVE-2020-14125 on June 6, 2022. “The downgrade issue,
which has been confirmed by Xiaomi to belong to a third-party
vendor, is being fixed,” Check Point added.
References
- ^
secure
enclave (en.wikipedia.org) - ^
said
(research.checkpoint.com) - ^
Tencent
Soter (github.com) - ^
patches
(trust.mi.com)
Read more https://thehackernews.com/2022/08/xiaomi-phones-with-mediatek-chips-found.html